Learn about Database Management System Short Question Notes from the B.Tech. AKTU Quantum Book. For effective and dependable data storage and retrieval, investigate data organisation, query optimisation, and transaction management.
Dudes 🤔.. You want more useful details regarding this subject. Please keep in mind this as well. Important Questions For Database Management System: *Quantum *B.tech-Syllabus *Circulars *B.tech AKTU RESULT * Btech 3rd Year * Aktu Solved Question Paper
Unit-I: Introduction (Short Question)
Q1. What are the functions of DBMS ?
Ans. The functions of DBMS are:
- i. The ability to update and retrieve data
- ii. Support concurrent updates
- iii. Recovery of data
- iv. Security
- v. Data integrity
Q2. List some applications of DBMS.
Ans. Applications of DBMS are:
i. Banking ii. Airlines
iii. Credit card transactions iv. Finance
v. Web based services vi. Telecommunications
Q3. What are the advantages of file processing system which were removed by the DBMS?
Ans.
- i. No problem of centralization
- ii. Less expensive
- iii. Less need of hardware
- iv. Less complex in backup and recovery
Q4. What is data model ? List the types of data model used.
Ans. A database’s data model is its logical organisation. It is a group of conceptual instruments for representing data, data connections, data semantics, and consistency requirements.
Types of data model used:
- 1. Hierarchical model
- 2. Network model
- 3. Relational model
- 4. Object-oriented model
- 5. Object-relational model
Q5. Write advantages of database.
Ans. Advantages of database:
- 1. Controlling data redundancy
- 2. Sharing of data
- 3. Data consistency
- 4. Integration of data
- 5. Integration constraints
- 6. Data security
Q6. Explain logical data independence.
Ans. Logical data independence is the separation of external views from conceptual views, allowing the user to change the conceptual view without affecting the external views or application software.
Q7. Define the term data redundancy and data consistency.
Ans. Data redundancy: Data redundancy is the occurrence of values for data elements more than once in a file or database.
Data consistency: Data consistency states that only valid data will be written to the database.
Q8. What do you mean by DML and DDL?
Ans. Data Manipulation Language (DML): A DML is a language that allows users to access and modify data that has been arranged according to the right data model. Common DML commands include insert, update, delete, and query.
Data Definition Language (DDL): In contrast to data, database structures can be created, modified, and deleted using the DDL set of SQL commands. The DBA typically makes use of them. Common DDL commands include create, truncate, drop, and edit.
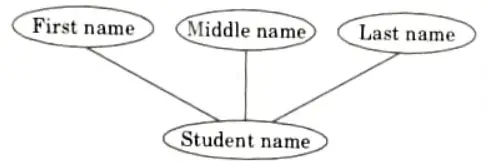
Q9. Give example of a simple, composite attributes of an entity.
Ans. Simple attribute: A simple attribute is an attribute composed of a single component with an independent existence. Example : Roll number, salary etc.
Composite attribute: An attribute composed of multiple components each with an independent existence is called a composite attribute.
Example : Name, which is composed of attributes like first name, middle name and last name.


Q10. Write the difference between super key and candidate key.
Ans.
| S. No. | Super key | Candidate key |
| 1. | A super key is a collection of one or more qualities that, when combined, enables us to uniquely identify a given entity inside the entity set. | A column or group of columns in the table that can be used to identify any database record without using any other data is known as a candidate key. |
| 2. | Super key is a broadest unique identifier. | Candidate key is a subset of super key. |
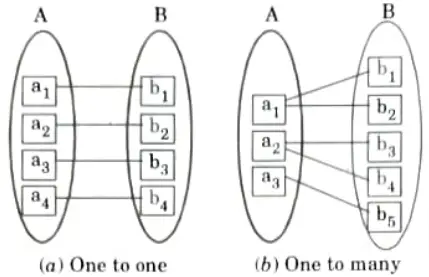
Q11. Give example for one to one and one to many relationships.
Ans.


Q12. Describe the purpose of foreign key.
Ans. The linkage between tables is established by using a foreign key. It is a field that connects the main key in one table to a field in another.
Q13. Explain specialization.
Ans. The process of specialisation involves adding additional traits to an existing class of objects in order to generate one or more new classes of objects. This entails taking a higher-level entity and creating lower-level entities by adding more attributes.
Q14. What do you mean by aggregation ?
Ans. Aggregation is an abstraction through which relationships are treated as higher level entities.
Q15. Define super key, candidate key, primary key and foreign key.
Ans. Super key: It is a set of one or more attributes that, taken collectively, allows us to identify uniquely an entity in the entity set.
Candidate key: A candidate key is a column, or set of column, in the table that can uniquely identify any database record without referring to any other data.
Primary key: Primary key is a candidate key that, is used for unique identification of entities within the table.
Foreign key: A foreign key is derived from the primary key of the same or some other table. Foreign key is the combination of one or more columns in a table (parent table) at references a in primary key another table (child table).
Q16. What is strong and weak entity set ?
Ans. Strong entity: Strong entities in a schema are independent of all other entities. Primary key is always present in strong entities. A single rectangle represents a strong entity. A solitary diamond symbolises the link between two powerful entities.
Weak entity: Strong entity is necessary for the continued existence of weak entity. Weak entity has a primary partial discriminator key instead of any key. Double rectangle represents a weak entity.
Q17. Explain the difference between a weak and a strong entity set with example.
Ans.
| S. No. | Weak entity set | Strong entity set |
| 1. | An entity set which does not possess sufficient attributes to from a primary key is called a weak entity set. | An entity set which does have a primary key is called a strong entity set. |
| 2. | It is represented by a rectangle. | It is represented by a double rectangle. |
| 3. | It contains a primary key represented by an underline. | lt contains a primary key represented by a dashed underline. |
Q18. Discuss three level of abstractions or schemas architecture of DBMS.
Ans. Different levels of data abstraction:
- 1. Physical level
- 2. Logical level
- 3. View level
Unit-II: Relational Data Model and Language (Short Question)
Q1.Define the term degree and cardinality.
Ans. Degree: The number of attributes in a relation is known as degree.
Cardinality: The number of tuples in a relation is known as cardinality.
Q2. What do you mean by referential integrity ?
Ans. While using the relational model, we frequently want to make sure that a value that occurs for a specific set of characteristics in one relation also shows for that same set of attributes in another relation. Referential integrity describes this situation.
Q3. Explain entity integrity constraints.
Ans. In accordance with the entity integrity requirement, primary keys cannot be empty. The primary key field needs to contain the right value. This is so because a table’s primary key value is utilised to distinguish between specific rows. Primary keys with null values would prevent us from being able to identify those rows.
Q4. Define foreign key constraint.
Ans. Some properties in one relation may relate to other attributes in another relation thanks to a foreign key constraint. The incomplete information is contained in the relation on which the foreign key constraint is defined.
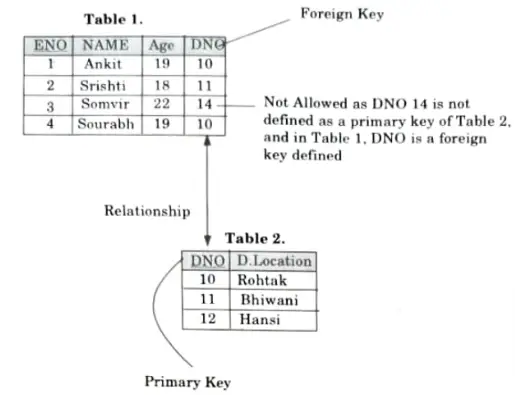
Q5. With an example show how a referential integrity can be implemented.
Ans. This rule states that if a foreign key in Table 1 refers to the primary key of Table 2, then every value of the foreign key in Table 1 must be null or be available in Table 2.


Q6. When do you get constraints violation ? Also, define null value constraint.
Ans. Constraints get violated during update operations on the relation.
Null value constraint: While creating tables, if a row lacks a data value for a particular column, that value is said to be null.
Q7. What is the role of join operations in relational algebra ?
Ans. The join operation, denoted by ⋈, is used to join two relations to form a new relation on the basis of a common attribute present in the two operand relations.
Q8. What are characteristics of SQL?
Ans. Characteristics of SQL:
- 1. SQL usage is extremely flexible.
- 2. It uses a free form syntax.
Q9. Give merits and demerits of SQL database.
Ans. Merits of SQL database:
- i. High speed
- ii. Security
- iii. Compatibility
- iv. No coding required
Demerits of SQL database:
- i. Some versions of SQL are costly.
- ii. Difficulty in interfacing
- iii. Partial control is given to database.
Q10. What is the purpose of view in SQL ?
Ans. A perspective is a virtual relation that derives its contents from other relations already in existence but does not physically exist. Although there are some restrictions on update operations, a view can be used similarly to any other relation in terms of querying, inserting into, deleting from, and joining with other relations or views.
Q11. Which command is used for creating user-defined data types ?
Ans. The user-defined data types can be created using the CREATE DOMAIN command.
Q12. What do you mean by query and subquery ?
Ans. Query is a request to database for obtaining some data. A subquery is a SQL query nested inside a larger query. Subqueries must be enclosed within parenthesis.
Q13. Write the purpose of trigger.
Ans. Purpose of trigger:
- 1. Automatically generate derived column values.
- 2. Prevent invalid transactions
- 3. Enforce complex security authorization.
- 4. Enforce referential integrity across nodes in a distributed database.
- 5. Enforce complex business rules.
Q14. What do you mean by PL/SQL?
Ans. PL/SQL stands for Procedural Language/SQL. PL/SQL extends SQL by adding constructs found in procedural languages, resulting is a structural language that is more powerful than SQL.
Q15. What is union compatibility ?
Ans. Two relation instances are said to be union compatible if the following conditions hold:
- i. They have the same number of the fields.
- ii. Corresponding fields, taken in order from left to right, have the same domains.
Q16. What is Relational Algebra ?
Ans. The relational algebra is a procedural query language. It consists of a set of operations that take one or two relations as input and produces a new relation as a result.
Q17. Define constraint and its types in DBMS.
Ans. A constraint is a rule that is used for optimization purposes.
Types of constraints:
- 1. NOTNULL
- 2. UNIQUE
- 3. DEFAULT
- 4. CHECK
- 5. Key constraints
- i. Primary key
- ii. Foreign key
- 6. Domain constraints
Unit-III: Database Design & Normalization (Short Question)
Q1. Distinguish between functional dependency and multivalued dependency.
Ans. Functional dependency:
A functional dependency, denoted by X → Y, between two sets of attributes X and Y that are subsets ofR specifies a constraint on the possible tuples that can form a relation, state r or R.
Multivalued dependency (MVD):
MVD occurs when two or more independent multivalued facts about the same attribute occur within the same relation. MVD is denoted by X →→Y specified on relation schema R, where X and Y are both subsets of R.
Q2. When are two sets of functional dependencies said to be equivalent?
Ans.
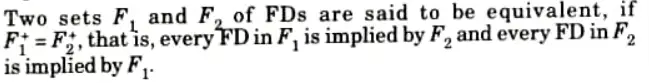
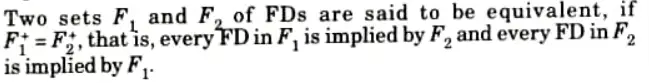
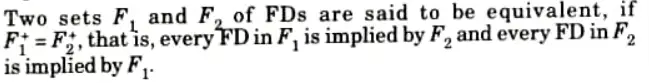
Q3. Define the following:
a. Full functional dependency
b. Partial dependency
Ans. a. A dependency X → Y in a relational schema R is said to be a fully functionally dependency if there is no A, where A is the proper subset of X such that A → Y. It implies removal of any attribute from X means that the dependency does not hold any more.
b. A dependency X → Y in a relational schema R is said to be a partial dependency if there is any attribute A where A is the proper subset of X such that A →Y. The attribute Y is said to be partially dependent on the attribute X.
Q4. What is transitive dependency ? Name the normal form which is based on the concept of transitive dependency.
Ans. An attribute Y of a relational schema R is said to be transitively dependent on attribute X (X → Y) if there is a set of attributes A that is neither a candidate key nor a subset of any key of R and both X → A and A → Y hold.
The normal form that is based on transitive dependency is 3NF.
Q5. What is normalization ?
Ans. Normalization is the process of organizing a database to reduce redundancy and improve data integrity.
Q6. Define 2NF.
Ans. A relation R is in second normal form (2NF) if and only if it is in INF and every non-key attribute is fully dependent on the primary key. A relation R is in 2NF if every non-prime attribute of R is fully functionally dependent on each relation key.
Q7. Why is BCNF considered simpler as well as stronger than 3NF ?
Ans. BCNP is the simpler form of 3NF as it makes explicit reference to neither the first and second normal forms nor to the concept ot transitive dependence.
In addition, it is stronger than 3NF as every relation that is in BCNF is also in 3NF but the vice versa is not necessarily true.
Q8. Define lossless join decomposition.
Ans. Let R be a relational schema and let F be a set of functional dependencies on R. Let R1 and R2 form a decomposition of R. This decomposition is a lossless join decomposition of R if at least one of the following functional dependencies is in F+.
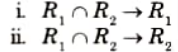
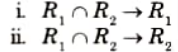
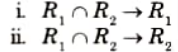
Q9. What do you understand by the closure of a set of attribute?
Ans. The closure of a set of attributes implies a certain subset of the closure that consists of all FDs with a specified set of Z attributes as determinant.
Q10. What are the uses of the closure algorithm ?
Ans. Besides computing the subset of closure, the closure algorithm has other uses that are as follows To determine if a particular FD:
- i. To determine if a particular FD, say X → Y is in the closure F+ of F, without computing the closure F+. This can be done by simply computing X+ by using the closure algorithm and then checking if Y⊆X+.
- ii. To test if a set of attributes A is a superkey of R. This can be done by computing A+ and checking if A+ contains all the attributes of R.
Q11. Describe the dependency preservation property.
Ans. No PD of the original relation is lost, which is a characteristic that is required during decomposition. The dependency preservation property makes sure that each FD represented by the original connection is upheld by looking at a single decomposed relation or by inferring FDs from other decomposed relations.
Q12. What are the various anomalies associated with RDBMS ?
OR
What are the different types of anomalies associated with database?
Ans. In RDBMS, certain update anomalies can arise, which are as follows:
- i. Insertion anomaly: As a result, unless additional information is stored, some information cannot be entered into a relation.
- ii. Deletion anomaly: As a result, if specific data representing certain information are deleted, associated data representing other information may also be lost.
- iii. Modification anomaly: If the same data are not also altered at other locations, repeating data modified at one location would result in inconsistency.
Q13. Why do we normalize database ?
Ans. We normalize database:
- 1. To avoid redundancy
- 2. To avoid update/delete anomalies
Q14. Are normal forms alone sufficient as a condition for a good schema design ? Explain.
Ans. No, the existence of normal forms alone is insufficient to guarantee a successful Schema design. For a design to be considered good, two more features, lossless Join property and dependency preservation property, must hold on decomposition.
Unit-IV: Transaction Processing Concept (Short Question)
Q1. Define transaction.
Ans. A transaction is a group of activities that together constitute a single logical unit of work. The requests to access, alter, add, or any combination of these requests for new data make up the operations that make up a transaction.
Q2. Define the term ACID properties.
Ans. A collection of characteristics for database transactions called ACID (Atomicity, Consistency, Isolation, Durability) is meant to ensure their validity even in the case of mistakes, power outages, etc.
Q3. State the properties of transaction.
Ans. ACID properties of transaction:
- i. Atomicity
- ii. Consistency
- iii. Isolation
- iv. Durability
Q4. Explain I in ACID property.
Ans. I in ACID property stands for isolation i.e., each transaction is unaware of other transaction executing concurrently in the system.
Q5. What is serializability ? How it is tested?
Ans. A schedule for performing concurrent transactions serially and in the same sequence is guaranteed by the traditional concurrency approach known as serializability. By creating a precedence graph, serializability is evaluated.
Q6. Define schedule.
Ans. A schedule is a list of actions (operations) carried out by a group of transactions that are carried out concurrently in the system, organized by time.
Q7. What do you mean by serial schedule ?
Ans. Serial schedule is a schedule in which transactions in the schedule are defined to execute one after the other.
Q8. Define replication in distributed database.
Ans. In distributed databases, replication is a technique used to store multiple copies of a data table at various locations.
Q9. Define data atomicity.
Ans. Data atomicity is one of the transaction attributes that indicates whether or not all of the transaction’s operations are correctly recorded in the database.
Q10. Define cascading rollback and blind writes.
Ans. Cascading rollback is a situation in which failure of single transaction leads to a series of transaction rollbacks.
Blind writes are those write operations which are performed without performing the read operation.
Q11. Give types of failures.
Ans. Types of failures:
- i. Transaction failure
- ii. System crash
- iii. Disk failure
Q12. Give the idea behind shadow paging technique.
Ans. The key idea behind shadow paging, technique is to maintain following two page tables during the life of transaction:
- i. Current page table
- ii. Shadow page table
Q13. Give merits and demerits of shadow paging.
Ans. Merits of shadow paging:
- i. The overhead of log record output is eliminated.
- ii. Recovery from crashes is significantly faster.
Demerits:
- i. Commit overhead
- ii. Data fragmentation
- iii. Garbage collection
Q14. What is multimedia database ?
Ans. Many types of multimedia information, such as images (pictures or drawings), video clips (movies, newsreels, home videos), audio clips (songs, phone messages, speeches), and documents, can be stored and accessed using functionalities provided by multimedia databases (books, articles).
Q15. Why is it desirable to have concurrent execution of multiple transactions
Ans. It is desirable to have concurrent execution of multiple transaction:
- i. To increase system throughput.
- ii. To reduce average response time.
Q16. What do you mean by conflict serializable schedule ?
Ans. Conflict serializable schedules are those that can be changed into serial schedules by Switching non-conflicting operations.
Q17. Define concurrency control.
Ans. Concurrency Control (CC) is a mechanism used in database management systems to guarantee that data is updated properly and accurately when numerous transactions are being carried out simultaneously.
Unit-V: Concurrency Control Techniques (Short Question)
Q1. Why is concurrency control needed ?
Ans. When several transactions are being processed simultaneously, concurrency control is necessary to ensure that the data is updated accurately.
Q2. Write down the main categories of concurrency control.
Ans. Categories of concurrency control are:
i. Optimistic ii. Pessimistic
iii. Semi-optimistic
Q3. What do you mean by optimistic concurrency control ?
Ans. When transactions commit with conflicts, optimistic concurrency control states indicate that the transaction fails. When conflicts are not anticipated, it is helpful, but if they do arise, the committing transaction is rolled back and can be begun again.
Q4. Define locks.
Ans. Each data item has a lock that serves as a variable to signal whether read or write operations are being used.
Q5. Define the modes of lock.
Ans. Data items can be locked in two modes:
- 1. Exclusive (X) mode: If a transaction Ti has obtained an exclusive mode lock on item Q, then Ti can read as well as write Q data item.
- 2. Shared (S) mode: If a transaction Ti has obtained a shared mode lock on item Q, then Ti can only read the data item Q but Ti cannot write the data item Q.
Q6. Give merits and demerits of two-phase locking.
Ans. Merits of two phase locking:
- i. It maintains database consistency
- ii. It increases concurrency over static locking as locks are held for shorter period.
Demerits of two-phase locking:
- i. Deadlock
- ii. Cascade aborts/rollback
Q7. Define lock compatibility.
Ans. Lock compatibility determines whether locks can be acquired on a data item by multiple transactions at the same time.
Q8. Define upgrade and downgrade in locking protocol.
Ans. Upgrade: Upgrade is the lock conversion from shared to exclusive mode. It takes place only in growing phase.
Downgrade: Downgrade is the lock conversion from exclusive to shared mode. It can take place only in shrinking phase.
Q9. Define the term intention lock.
Ans. A transaction that aims to explicitly lock a lower level of the tree is said to be using an intention lock, a sort of lock mode utilised in multiple granularity locking. Intention mode works with shared mode and exclusive mode to offer a higher level of concurrency.
Q10. What are the pitfalls of lock based protocol?
Ans. Pitfalls of lock based protocols are:
- i. Deadlock can occur.
- ii. Starvation is also possible if concurrency control manager is badly designed.
Q11. Define exclusive lock.
Ans. Exclusive lock is a lock which provides only one user to read a data item at a particular time.
Q12. Define timestamp.
Ans. The DBMS generates a timestamp as a special identifier to identify transactions. In timestamp-based concurrency control strategies, this timestamp is employed.
Q13. Define multiversion scheme.
Ans. A scheme known as multiversion concurrency control creates a new version of Q with each write(Q) operation. The concurrency control manager chooses one of the versions of Q to be read in a transaction that requests a read (Q) operation and ensures serializability.
Q14. Define Thomas’ write rule.
Ans. Thomas’ write rule is a modification to the basic timestamp ordering that differs slightly from the basic timestamp ordering’s rules for write operations. There is no requirement for conflict serializability.



Important Question with solutions | AKTU Quantums | Syllabus | Short Questions
Database Management System Btech Quantum PDF, Syllabus, Important Questions
| Label | Link |
|---|---|
| Subject Syllabus | Syllabus |
| Short Questions | Short-question |
| Question paper – 2021-22 | 2021-22 |
Database Management System Quantum PDF | AKTU Quantum PDF:
| Quantum Series | Links |
| Quantum -2022-23 | 2022-23 |
AKTU Important Links | Btech Syllabus
| Link Name | Links |
|---|---|
| Btech AKTU Circulars | Links |
| Btech AKTU Syllabus | Links |
| Btech AKTU Student Dashboard | Student Dashboard |
| AKTU RESULT (One VIew) | Student Result |

3 thoughts on “Btech Aktu Database Management System KCS-501 Short Question Pdf”