Mobile Computing: AKTU question paper with answers provides a comprehensive set of exam-oriented questions and lengthy solutions to assist B.Tech students in preparing for mobile computing-related exams.
Dudes 🤔.. You want more useful details regarding this subject. Please keep in mind this as well. Important Questions For Mobile Computing: *Quantum *B.tech-Syllabus *Circulars *B.tech AKTU RESULT * Btech 4th Year
Section A: Repeated Short Questions in Mobile Computing
a. What are HLR and VLR in mobile computing ?
Ans. Home Location Register (HLR) :
The HLR is a database used for subscription storage and management. HLR keeps subscriber data indefinitely, including a subscriber profile, location information, and activity status.
Visitor Location Register (VLR) :
The VLR is a database that holds transitory information on subscribers that the MSC (Mobile Switching Centre) requires in order to deliver service to visiting subscribers. The VLR is a live database that is linked to each MSC.
b. What is the purpose of handoff in mobile communication ?
Ans. The process of transferring an active call or data session from one cell in a cellular network to another, or from one channel in a cell to another, is referred to as a handoff.
c. Explain near and far problem in context to cellular network.
Ans.
- 1. All signals in CDMA systems are transmitted at the same time on the same frequency band.
- 2. When all mobiles broadcast at the same power level to the base station, the strength of a nearby (unwanted) mobile arriving at the listening base station overwhelms the signal from a distant (wanted) mobile.
- 3. The near-far problem is the fundamental impediment to the implementation of CDMA cellular systems.
d. What is mobile IP ?
Ans. Mobile IP (or IP mobility) is a standard communication protocol that allows mobile device users to move from one network to another while keeping their IP address constant. This protocol allows IP datagrams to be routed on the internet regardless of their location.
e. What is adaptive clustering ?
Ans. Adaptive clustering operates on quick and deployable wireless network infrastructure. It was completely asynchronous and used a distributed architecture. Multihopping is one of the characteristics of adaptive clustering.
f. What is Bluetooth ?
Ans. Bluetooth is an open wireless technology standard for sharing data over short distances (through short wavelength radio transmission) between stationary and mobile devices, resulting in highly secure personal area networks (PANs).
g. What is wireless application protocol ?
Ans. Wireless application protocol (WAP) connects mobile and wireless devices to the internet. WAP’s purpose is to offer internet content like web pages and phone services to digital cellular phones and other wireless terminals like laptops and PDAs.
h. What is meant by transaction processing ?
Ans. Transaction processing is the division of information processing into discrete and unseen operations known as transactions. It is intended to keep databases in a known, consistent state by ensuring that all interdependent operations on the database are either completed successfully or terminated effectively.
i. Define fisheye state routing.
Ans. GSR is improved by FSR (both are based on the link state protocol). The high size of GSR update messages wastes a significant amount of network capacity. This technique was developed to minimize the amount of data needed to depict graphical data.
j. Describe Temporary Ordered Routing Algorithm (TORA) in brief.
Ans. The TORA routing algorithm is a source-initiated on-demand routing method. It is a highly adaptive, efficient, and scalable distributed routing algorithm that is based on the link reversal notion. This protocol is primarily intended to reduce the impact of topology changes.
Section B : Aktu Long Questions in Mobile Computing
a. What is general packet radio service (GPRS) ? Describe its architecture in detail.
Ans. GPRS (General Packet Radio Service) :
- 1. GPRS is a mobile device-based packet-based communication service that allows data to be delivered and received through a mobile telephone network.
- 2. GPRS served as the initial stepping stone between second-generation GSM cellular technology and the 3G-W-CDMA/UMTS system.
- 3. GPRS is a mobile data service provided to GSM and IS-136 phone customers.
- 4. GPRS data transfer is often charged per megabyte of transferred data, whereas traditional circuit switching data communication is invoiced per minute of connection time, regardless of whether the user has actually transferred data.
- 5. GPRS can be used for WAP access, SMS, MMS, as well as internet communication services such as e-mail and online access.
- 6. GPRS may provide data speeds ranging from 14.4 kbps to 171.2 kbps, allowing for convenient internet access.
- 7. It supports both short “bursty” traffic, such as e-mail and web browsing, and enormous amounts of data.
- 8. A dial-up modem connection is not required for GPRS.
- 9. It provides a quick set-up mechanism to provide the impression of being “always on.”
GPRS architecture :
- 1. GPRS uses the GSM architecture for voice.
- 2. To provide packet data service via GPRS, a new class of network nodes must be established as an upgrade to the existing GSM network.
- 3. These network nodes are referred to as GPRS support nodes (GSN).
- 4. GPRS support nodes are in charge of data packet delivery and routing between mobile stations and the external packet data network (PDN).
b. Describe the architecture, protocol stack and applications of wireless application protocol.
Ans. Architecture / Protocol stack of WAP :
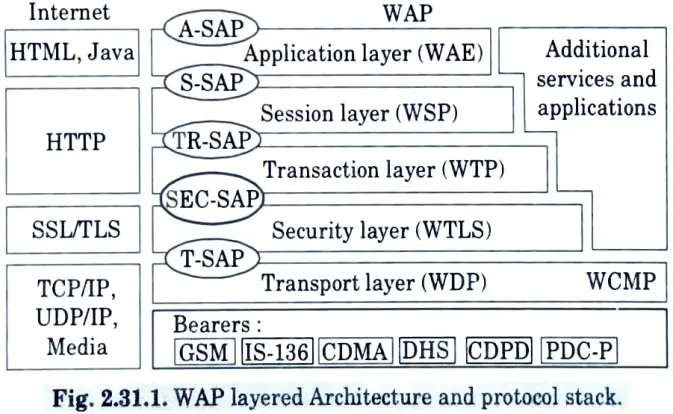


Wireless Application Protocol (WAP) :
- 1. WAP offers internet access to mobile and wireless devices.
- 2. WAP’s purpose is to offer internet content, such as web pages and phone services, to digital cellular phones and other wireless terminals, such as laptops and PDAs.
- 3. In 1997, Ericsson, Motorola, and Nokia established the WAP forum to develop frame standards and protocol specifications.
- 4. WAP incorporates a lightweight web browser called MICRO browser into hand-held devices with low computing and memory capacity.
- 5. Several constraints in mobile wireless network in order to access internet from mobile phone are :
- a. Size and weight of mobile equipment (portable).
- b. Restricted user interface (small keypad and displays, lower memory).
- c. Limited bandwidth and lower reliability due to high error data.
- d. Different WAP sets (different screen size and features).
- e. Different wireless bearer network like GSM, CDMA, GPRS.
- f. Security and integrity of user data, protection of services.
- 6. The primary goals of WAP are to offer different internet content (such as web pages and push services) and other data services (such as stock quotes) to digital cellular phones and other wireless, mobile terminals (for example, PDAs, laptops).
- 7. Furthermore, a protocol suite should support worldwide wireless communication across various wireless network technologies, such as GSM, CDPD, UMTS, and so on.
- 8. Wherever practical, the forum embraces and extends current internet standards and technologies, and it is developing a framework for the development of content and applications that scale over a wide range of wireless bearer networks and wireless device types.
WAP applications :
- 1. Handling information of all types.
- 2. Access to e-mail and chat.
- 3. Weather information.
- 4. Information about currency rates.
- 5. Online music support of WAP multimedia etc.
c. What is data replication ? Describe the replication strategies in detail.
Ans. Data replication :
- 1. Data replication creates and manages numerous copies of data at one or more locations, allowing an organization to exchange corporate data across its organization.
- 2. It acts as a backup system in the event of a system failure.
- 3. Data replication is a technique that was first employed in conventional dispersed environments to improve data availability and system performance.
- 4. These environments are distinguished by a fixed infrastructure in which the user employs fixed machines with adequate resources that are permanently connected to the network.
- 5. These properties have not been validated in mobile contexts.
- 6. In this situation, consumer devices like laptops, PDAs, and mobile phones have limited memory, disc space, battery power, and process or capacity.
- 7. Because of these constraints, the replication system may be unable to create and place replicas on the user device.
- 8. In a mobile context, the user may potentially switch devices in order to access a service.
- 9. As a result, the variety of devices and, as a result, the context of use of services or an application must be considered.
- 10. In fact, mobile environments are characterised by a frequent shift in their resources, which can be attributed to a variety of factors such as the nature of the wireless network itself, user mobility, and multi-terminal access.
- 11. This modification may have an impact on data replication because the development and access to these data may necessitate a number of resources.
- 12. Confidential data, such as credit card numbers, should not be copied and transmitted over insecure nodes and networks.
- 13. As a result, differences in the level of security may prevent the user from accessing this data.
- 14. As a result, a traditional system is unable to meet the client’s need.
- 15. To maintain service continuity, replication system operations such as creation, placement, read, write, and consistency operation must be tailored to all resource variations that data may require.
d. Discuss challenges in transaction processing. What are the counter measures to security threats in mobile computing environment ?
Ans. Challenges in transaction processing :
- 1. Enhanced failure model :
- a. As compared to fixed-wired networks, mobile environments have a number of failures: Message loss occurs in fixed wired networks as a result of uncommon events such as buffer overflows or data packet collisions.
- b. Message loss, on the other hand, is more common on mobile networks.
- c. For example, if the sender or receiver moves out of range, if the channel is interfered with, if impediments obstruct transmission, or if the sender’s or receiver’s battery abruptly discharges during message transmission.
- d. Network partitioning owing to participant movement occurs more frequently in mobile environments than in fixed-wired networks, where this occurrence occurs very seldom.
- 2. Message reception model :
- a. A message transmitted through a mobile adhoc network is not only received by the intended recipient.
- b. The message can be heard by all participants who are close to the sender.
- c. When a routing strategy is implemented, participants who are close to the message’s path will receive the message.
- 3. Device controllability :
- a. Distributed databases are typically utilised on fixed-wired networks for performance and availability reasons.
- b. As a result, there is frequently a single database owner that controls all of its databases.
- c. Yet, with mobile networks, each user owns and controls only one device.
- d. Because there is no central instance that governs the devices in a wireless network, we cannot ensure that all individual users cooperate and do not leave.
- 4. Compensation applicability :
- a. Transaction processing models that use the concept of compensation explicitly allow databases to enter potentially contradictory states that are later compensated for.
- b. Nevertheless, compensation models imply that databases are somehow linked to a single location that handles compensation.
- c. As a result, participants with inconsistent states will refuse to join in subsequent transactions with different participants until their inconsistent states are compensated.
- 5. Capabilities: The mobile devices have limited capabilities like memory, processing, and storage constraints.
- 6. Input mechanism(s) :
- a. The most common input mechanisms for mobile devices are built in keypads, pens and touch screen interfaces.
- b. Usually, PDAs contain software keyboards, some PDAs may also support external keyboards.
- 7. Network stack
Measures to security threats in computing environment :
- 1. Agent-to-Platform: The agent-to-platform category represents the set of threats in which agents exploit security weakness of an agent platform or launch attacks against an agent platform.
- 2. Agent-to-Agent: Agent-to-Agent category represents the set of threats in which agents exploit security weakness of other agents or launch attacks against other agents.
- 3. Platform-to-Agent: The platform-to-agent category represents the set of threats in which platform compromise the security of agents.
- 4. Other-to-Agent Platform: The other-to-agent platform category represents the set of threats, in which external entities, including agents and agent platforms, threaten the security of an agent platform.
e. What do you understand by Mobile Ad-Hoc Networks (MANET) ? Describe some real life scenarios where it can be used.
Ans.
- 1. MANET is a self configuration wireless adhoc network of mobile nodes.
- 2. Each node has a router or a switch connected by the wireless connection.
- 3. The union of connections is in an arbitrary topology.
- 4. Network can function independently or connect to internet IPv4 or IPv6.
- 5. The MANET organization depends upon the location of the nodes, their connectivity, their service discovery capability and their ability to search and route messages using nearest node or nearby nodes.
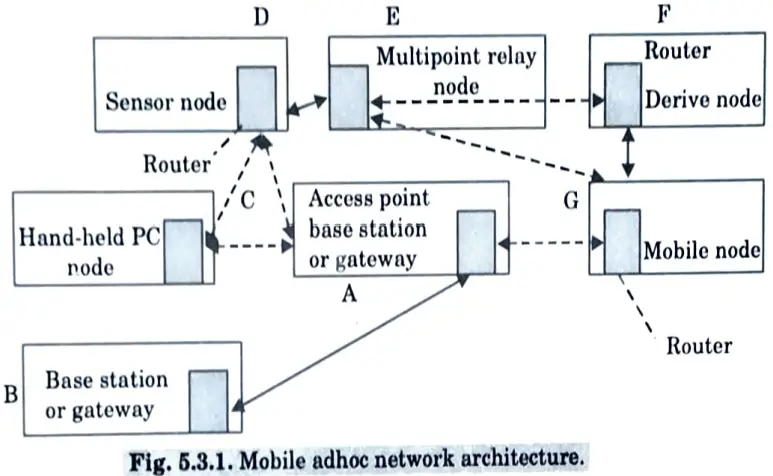


Description :
- 1. Fig. 5.3.1 demonstrates the adhoc network formed by the nodes A, B, C, D, E, F and G.
- 2. It demonstrates how each mobile device or sensor acts as a node connected to a switch or router.
- 3. An significant feature of adhoc network design is that its organization can change as a result of a device or sensor moving.
- 4. In other words, ad hoc networks self-organize.
- 5. The following points illustrate how MANETs are established and how they recognize themselves.
- a. The network organization will change if D and E move away from each other such that they reach out of the range of wireless coverage.
- b. Two new adhoc networks will then be formed by (i) A, C andD, (ii) A, G, F and E. The devices on two networks can still connect to each other through the common node A.
Real life scenario :
- 1. Consider a Bluetooth-enabled mobile device, a Bluetooth-enabled computer, and a home internet connection with Wi-Fi.
- 2. At the office, there is a bluetooth-enabled computer that is connected to the TCP/IP internet as well as a client printer.
- 3. When the user transfers from the office to the home and the handheld PDA mobile device comes close to the home computer, an adhoc network is established between the mobile device at home and the printer at the office via intermediate nodes such as Wi-Fi, the internet, and the office computer.
Section 3 : SDMA, TDMA, FDMA and CDMA in Mobile Computing
a. What are the various characteristics of mobile computing ? Discuss challenges being faced to support mobile computing.
Ans. Characteristics of mobile computing :
- 1. User mobility: User should be able to move from one physical location to another location and use the same service.
- 2. Network mobility: User should be able to move from one network to another network and use same services.
- 3. Bearer mobility :
- a. Bearer services are in charge of data transmission between two user network interfaces. In the case of bearer mobility, the user should be able to move from one bearer to another while continuing to access the same services.
- b. Several sorts of transport bearers exist for different types of networks. TCPIP and HTTP protocols can be used for dial-up connections. SMS and WAP could be used for GSM, whereas voice will be used for mobile.
- 4. Device mobility: User should be able to move from one device to another and use the same service.
- 5. Service mobility: User should be able to move from one service to another.
- 6. Host mobility: The user device can either be a client or server. In case of host mobility the mobility of IP needs to be taken care off.
Challenges faced by mobile computing :
There are a number of technical challenges that mobile computing faces and it has to overcome them. Some of them are :
1. Mobility :
This is the important aspect of mobile computing, but there are certain challenges that, it has to face, these are :
- a. Auto configuration of the system, as the system keeps changing its environment. Hence, it has to configure itself to the new environment each time.
- b. Location management, again due to mobility location management becomes a challenge. As the following tasks are to be done frequently :
- i. Lookups (Track users call)
- ii. Updates (Updates user’s position and/or data)
- c. Heterogeneity, as the system keeps in a variety of environments, heterogeneity is also a challenge.
- d. Security authentication
- e. Spectrum range
2. Wireless medium :
As in mobile computing the transmission medium is wireless, therefore the following points are considered :
- a. Cost of networks
- b. Quantity and reliability of bandwidth
c. Environment obstacles
3. Portability :
Since the devices are also mobile therefore the following mobile restrictions are to be considered :
- a. Low resources
- b. Battery constraints
- c. Lack of security
b. Compare SDMA, TDMA, FDMA and CDMA in terms of transmission techniques, signal separation and applications ?
Ans. Comparison of SDMA, TDMA, FDMA and CDMA :
SDMA :
- i. Idea: Segment space into cells/sectors.
- ii. Terminals: Only one terminal can be active in one cell/one sector.
- iii. Signal Separation: Cell structure directed antennas.
- iv. Advantages: Very simple, increase capacity per km2.
- v. Disadvantages: Inflexible, antennas typically fixed.
- vi. Comment: Only in combination with TDMA, FDMA or CDMA useful.
TDMA :
- i. Idea: Segment sending time into disjoint time-slots, demand driven or fixed patterns.
- ii. Terminals: All terminals are active for short periods of time on the same frequency.
- iii. Signal Separation: Synchronization in the time domain.
- iv. Advantages: Established, fully digital, very flexible.
- v. Disadvantages: Guard space needed, synchronization difficult.
- vi. Comment: Standard in fixed networks, together with FDMA/SDMA used in many mobile networks.
FDMA :
- i. Idea: Segment the frequency band into disjoint sub-bands.
- ii. Terminals: Every terminal has its own frequency, un-interrupted.
- iii. Signal Separation: Filtering in the frequency domain.
- iv. Advantages: Simple, established, robust.
- v. Disadvantages: Inflexible, frequencies are a scarce resource.
- vi Comment: Typically combined with TDMA and SDMA.
CDMA :
- i. Idea: Spread the spectrum using orthogonal codes.
- ii. Terminals: All terminals can be active at the same place at the same moment, un-interrupted.
- iii. Signal Separation: Code plus special receivers.
- iv. Advantages: Flexible, less planning needed, soft handover.
- v. Introduction Disadvantages: Complex receivers, needs more complicated power control for senders.
- vi. Comment: Used in many 3G systems, higher complexity, lowered expectations, integrated with TDMA/FDMA.
Section 4 : Architecture of 802.11 L N in Mobile Computing
a. With neat sketch, explain architecture of 802.11 L N and explain its MAC logic.
Ans. Protocol architecture of IEEE 802.11 :
- 1. IEEE 802.11 fits seamlessly into the other 802.x standards for wired LANs as shown in Fig.2.12.2
- 2. This is most common scenario where an IEEE 802.11 wireless LAN connected to a switched IEEE 802.3 ethernet via a bridge.
- 3. The higher layers (application, TCP, IP) look the same for wireless nodes as for wired nodes.
- 4. The upper part of the data link control layer, the logical link control (LLC), covers the differences of the medium access control layers needed for the different media.
- 5. In many of today’s networks, no explicit LLC layer is visible.
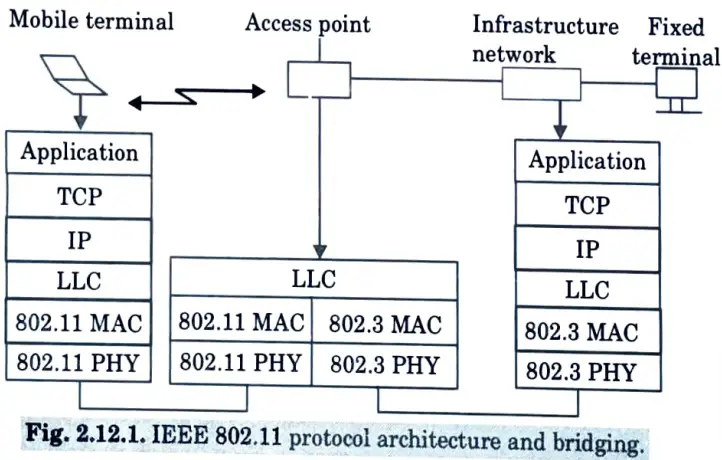


- 6. The IEEE 802.11 standard only covers the physical layer PHY and medium access layer MAC like the other 802.x LANs do.
- 7. The physical layer is subdivided into the “physical layer convergence protocol (PLCP)” and the “physical medium dependent sub-layer (PMD)”.
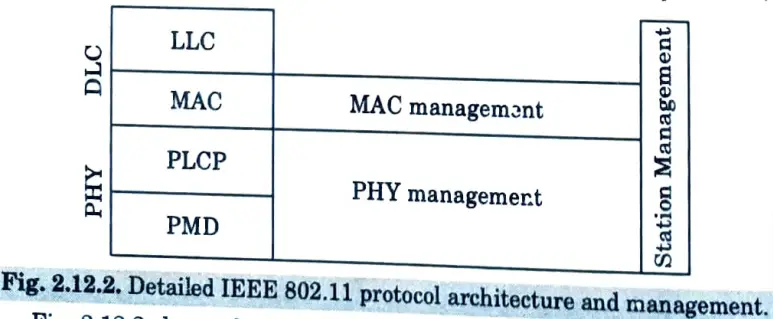


- 8. Fig. 2.12.2 shows the IEEE 802.11 layers along and the protocol sub layer and MAC, PHY and station management.
- a. MAC management :
- i. This allows a station to be associated and de-associated with an access point.
- ii. It also manages synchronisation, roaming of a station in relation to an access point, and power management in order to conserve battery power.
- iii. MAC management also keeps the MAC management knowledge base up to date (MIB).
- b. PHY management: This is responsible for channel selection and PHY-MIB maintenance.
- c. Station management: This is responsible for coordination of all management functions and additional higher layer functions.
MAC protocols: There are two basic 802.11 MAC protocols described as follows :
- 1. DCF :
- a. The basic 802.11 MAC protocol is the DCF based on CSMA.
- b. In DCF, after detecting that there is no other transmission on the channel, stations send MAC service data units (MSDUs) of arbitrary length up to 2304 bytes.
- c. A collision happens if two stations find the channel free at the same moment.
- d. The 802.11 standard specifies a collision avoidance (CA) technique to lessen the likelihood of such collisions.
- 2. PCF :
- a. In PCF, a point coordinator (PC), which requires an access point control, the medium access based on polling scheme in such a way that the point coordinator polls various stations to allow access to the medium based on their requirements.
- b. Because stations in PCF do not compete for the medium and medium access is managed centrally, the access method is frequently referred to as contention-free channel access.
b. Why does traditional TCP not perform well in wireless network ? Discuss different approaches for TCP improvement.
Ans. A. Performance of TCP over wireless network: A number of inherent characteristics of wireless media affect TCP performance including :
- 1. Channel losses :
- a. Wireless media signals are prone to severe interference from other signals, resulting in losses owing to bit alteration while frames are being delivered.
- b. TCP performance is impacted by frequent link layer losses since TCP automatically assumes all losses are caused by congestion and calls congestion control methods upon detecting any loss.
- b. Low bandwidth :
- a. Wireless link bandwidth may be limited, resulting in severe buffering at the base station.
- b. As a result, packets may be discarded at the base station or transported back and forth on the wireless link, resulting in long observed round trip times.
- 3. Signal fading: Fading typically occurs when a wireless host is mobile.
- 4. Movement across cells :
- a. A wireless host’s mobility includes handling connection handoff.
- b. In addition to the link layer state that must be passed on, the base station may keep connection state concerning the transport layer that must be passed on.
- 5. Channel asymmetry :
- a. Resolving channel contention is usually asymmetric.
- b. The transmitting entity receives greater transmission time than the receiving entity.
- c. This could result in TCP acknowledgements being queued for transmission at the receiving entity’s link layer and sent back to back when channel access is authorised.
- d. This might result in longer round trip times assessed by the TCP sender and bursty traffic, which decreases the TCP connection’s throughput.
- 6. Link latency: Wireless networks can have long latencies, and when these delays account for a considerable portion of the total round trip times recorded by TCP, the retransmission time outs are set to high numbers, affecting TCP performance.
B. Different approaches for TCP improvement: The various models proposed to improve TCP’s performance over wireless networks are as follows :
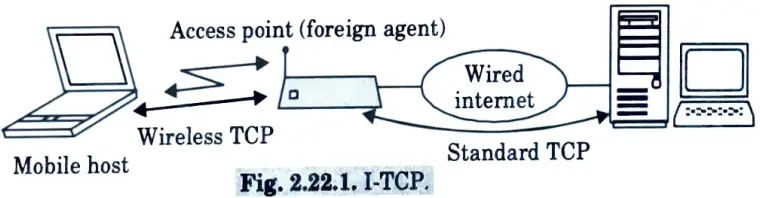
- 1. Indirect TCP :
- a. With I-TCP a transport layer connection between a mobile host and fixed host is established as two separate connections :
- i. One over the wireless link and
- ii. The other over the wired link with a “mobile support router” serving as the center point.
- b. Sender packets are buffered at the mobile support router until they are transferred through the wireless connection.
- c. A handoff method is provided to deal with the circumstance where the wireless host switches between cells.
- d. As a result of employing I-TCP, the TOCP ACKs are not end-to-end, which violates TCP’s end-to-end semantics.
- e. For hosts connected to the wired internet, indirect TCP or I-TCP segments the connection with no changes to the TCP protocol; millions of computers use (variants of) this protocol.
- f. It uses an optimized TCP protocol for mobile hosts.
- g. Hosts in the fixed part of the net do not notice the characteristics of the wireless part.
- a. With I-TCP a transport layer connection between a mobile host and fixed host is established as two separate connections :


- 2. Snooping TCP :
- a. One of the drawbacks of I-TCP is the segmentation of the single TCP connection into two TCP connections.
- b. This loses the original end to end TCP semantic.
- c. Snooping TCP works transparently and hence does not lose end to end semantics.
- d. The enhancement’s primary function is to buffer packets adjacent to the mobile host in order to execute quick local retransmission.
- e. Lost packets on the wireless link (both ways) will be retransmitted instantly by the foreign agent’s mobile host (so-called “local” retransmission); the foreign agent therefore “snoops” the packet flow and recognises acknowledgements in both directions.
- f. In snooping TCP, data transfer to the mobile host occurs as follows: the Foreign Agent (FA) buffers data until it receives the Mobile Host (MH) ACK, FA detects packet loss via duplicated ACKs or time out, and then quick retransmission is allowed, transparent to the fixed network.
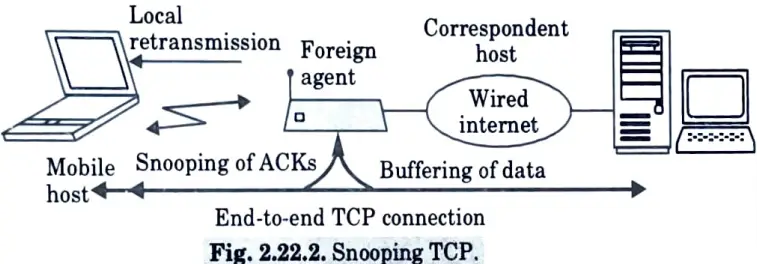


- g. When the FA detects packet loss on the wireless link via sequence numbers, data transfer from the mobile host occurs, and the FA responds directly with a NACK to the MH. MH can now retransmit data with minimal delay.
- h. Problems with snooping TCP :
- i. Snooping TCP does not isolate the wireless link as good as ITCP
- ii. Snooping might be useless depending on encryption schemes.
- 3. Mobile TCP :
- a. Mobile TCP (M-TCP) employs a split connection-based technique while attempting to retain end-to-end semantics. M-TCP employs a three-tiered hierarchy.
- b. At the most basic level, mobile hosts connect with mobile support stations in each cell, which are managed by a “supervisor host.”
- c. The supervisor host is linked to the wired network and functions as the connection’s splitter.
- d. A TCP client exists at the supervisor host.
- e. The TCP client gets the segment from the TCP sender and forwards it to a M -TCP client, which transmits it to the wireless device.
- f. Hence, normal TCP is used between the sender and the supervisor host, while M-TCP is utilised between the supervisor host and the wireless device.
- g. M-TCP is intended to fast recover from wireless losses caused by disconnections and to eliminate serial timeouts.
- h. TCP on the supervisor host does not accept received ACK packets until the wireless device acknowledges them.
- i. This preserves end-to-end semantics, the sender timeout estimate based on the entire round trip duration, and supports host mobility with minimal state mutation.
Section 5 : Data Management in Mobile Computing
a. What is data management in computing? Describe the data management issues in detail.
Ans. Data management issues in mobile computing :
- i. In mobile computing, mostly mobile technology support broadcast data management mechanism.
- ii. A server broadcast information to all mobile clients in its cell.
- iii. On the other hand, clients only access data when needed.
- iv. These two facts introduce new mechanism for data management different from the traditional algorithms proposed for traditional client server distributed database system.
- v. There are various issues in data management :
- 1. Mobility (Location Management)
- 2. Wireless medium
- 3. Cache consistency and data replication
- 4. Broadcasting and data management
- 5. Transaction management
- 6. Wireless security issues
- 7. Portability of mobile devices
- 8. Issues related to QoS (Quality of Service)
1. Mobility :
The location of mobile elements and therefore their point of attachment to the fixed network change as they move. So, in location management the following issues arise :
- a. How to know the current position of mobile unit ?
- b. Where to store location information ?
- c. Who should be responsible for determination and updation of information?
i. Location management :
The configuration of a system that includes mobile element is not static. So in designing distributed algorithm we can no more rely on a fixed topology.
- a. To locate the user, a distributed location database is used, which keeps track of the mobile user’s present location.
- b. Efficient data surfaces, algorithms, and query execution plans must be developed to describe, manage, and query the location of mobile elements, which is a rapidly changing data set.
- c. Location management entails searching, reading, and updating data.
ii. Heterogeneity :
- a. Connectivity’s performance and reliability become highly variable.
- b. For example, outside, a mobile client may have to rely on a low bandwidth network, whereas inside a building, it may be provided with consistent high bandwidth access.
- c. The number of devices in a network cell fluctuates with time, as do the base station load and bandwidth availability.
2. Wireless medium :
Wireless networks are more expensive, offers less bandwidth, and are less reliable than wireline networks.
a. Weak and intermittent connectivity :
- i. Wireless communication confronts numerous challenges because the signal interacts with its surroundings.
- ii. Since bandwidth is shared among users sharing a cell, the deliverable bandwidth per user is reduced.
- iii. Data transmission over air is currently monetarily expensive.
b. Variant connectivity :
i. Wireless technologies vary on the degree of bandwidth and reliability they provide.
c. Broadcast facility :
i. There is a high bandwidth broadcast channel from the base station to all mobile clients in its cell.
d. Tariffs :
i. Network access is charged per message in some networks (for example, packet radio), whereas it is charged per connection time in others (for example, in cellular telephones).
3. Portability :
a. Mobile elements are resource poor when compared to static elements :
- i. Movable elements must be light and tiny in order to be conveniently transported.
- ii. Because of this consideration, mobile elements will have fewer resources than static elements, such as memory, screen size, and storage capacity.
- iii. As a result, there is asymmetry between static and movable parts.
b. Mobile elements rely on battery :
- i. Despite breakthroughs in battery technology, this worry will persist.
- ii. Power consumption must be considered at multiple levels of hardware and software design.
- iii. Movable elements are more easily damaged, stolen, or misplaced. As a result, they are less secure and dependable than static parts.
4. Cache consistency and data replication :
- a. Caching is useful in mobile computing during frequent movement and connection to different database servers.
- b. Caching frequently requested data items is a critical strategy for reducing contention on tiny wireless networks.
- c. This will enhance query response time and allow for disconnected or poorly connected activities to be supported.
- d. Cache consistency is jeopardized by client disconnection and mobility, because a server may be uninformed of the client’s present position and connection state.
- e. The server can handle this problem by broadcasting either the real data, an invalidation report, or even control information such as log tables or logs on a regular basis.
- f. Data object replication is required to improve availability and performance.
- g. Support for detached mode, data divergence, application defined reconciliation methods, and optimistic concurrency management is required for replicated systems.
- h. Replication caused numerous challenges due to moved data and user and service mobility:
- i. How to manage data replications, providing the level of consistency, durability and availability needed ?
- ii. How to locate objects of interest ?
- iii. What are the conditions under which we need to replicate the data on a mobile site?
5. Broadcasting and data management :
- a. Broadcast scheduling is another issue to investigate.
- b. In general, the more data that is broadcast, the more requests that are served from the data broadcast, and thus reduces the likelihood of mobile clients sending the request to the server.
- c. However, if there is too much data in the broadcast cycle, the advantage of the broadcast data will be lessened.
- d. As a result, query response time would suffer as mobile users must wait for a significant amount of time before receiving the needed data.
- e. As a result, because the query access pattern changes dynamically, it is critical to decide what data to broadcast that serves the majority of the queries.
- f. Data broadcast can be managed with three different modes : On demand (pull-based), push-based and hybrid.
6. Transaction management :
A transaction in mobile environment is different than the transaction in the centralized or distributed database in the following ways :
- a. Mobile transactions may be required to divide their calculations into sets of operations, some of which execute on a mobile host and others on a stationary host.
- b. Due to disconnection and mobility, a mobile transaction shares its states and partial results with other transactions.
- c. The stationary host must provide computations and communications for mobile transactions.
- d. As the mobile host moves from one cell to the next, the state to transaction, states of accessible data items, and location information move with it.
- e. Because of the mobility of both data and users, as well as frequent disconnections, mobile transactions have a long life.
- f. The mobile transaction should support and handle concurrency recovery, disconnection and mutual consistency of replicated data object.
7. Wireless security issues :
To build an information security system, the following issues are raised :
- a. Who is the attacker ?
- b. What are the vulnerabilities ? What are the weak links in the system ?
- c. What could be the possible exploitations of these vulnerabilities by the resulting attack?
- d. What need special protection?
- e. To protect our assets from attack how much does the security system cost in terms of money resources and time ?
- f. When security system is deployed, to what extent will it affect the openness and add to inconvenience ?
- g. Is prevention better than cure ? If prevention is expensive or impractical, what is the strategy to recover from the loss following an attack ?
8. Issues relating to Quality of Service :
- a. Network connectivity has an impact on the Quality of Service (QoS) in a mobile network.
- b. Quality of service tools assess bandwidth availability, which influences data transfer rates, connection dependability, and data-loss hazards.
- c. QoS-aware mobile device applications. In distributed multimedia streams, quality of service (QoS) is a significant factor.
- d. Quality of service is critical for sustaining visual presentations on small screens in the event of connectivity and frame loss.
b. Describe the file system in mobile computing. How disconnected operations are performed in CODA file system ?
Ans.
- 1. CODA was created with the goal of becoming a scalable, secure, and highly available distributed file system.
- 2. A key goal was to establish a high degree of naming and location transparency, so that the system seemed to users as if it were a pure local file system.
- 3. CODA’s designers attempted to provide a high level of failure transparency by taking high availability into account.
- 4. CODA is a descendant of the Andrew file system (AFS) version 2 and shares many of its architectural features.
- 5. CODA follows the same organization as AFS.
- 6. Each Virtue workstation contains a user-level process named Venus, which performs comparable functions to an NFS client.
- 7. A Venus process is in charge of providing access to files hosted by Vice file servers.
- 8. In CODA, Venus is also in charge of allowing the client to keep running even if access to the file servers is (temporarily) unavailable.
- 9. This extra duty is a significant departure from the technique used in NFS.
- 10. The crucial point is that Venus runs as a user-level process.
- 11. Once again, a separate Virtual File System (VFS) layer intercepts all calls from client applications and routes them to either the local file system or Venus. This VES arrangement is the same as in NFS.
- 12. Venus, in turn, uses a user-level RPC protocol to interface with Vice file servers. The RPC system is built on UDP datagrams and supports at-most-once semantics. Three distinct server-side processes exist. The real Vice file servers, which are in charge of managing a local collection of files, do the vast majority of the labour.
- 13. A file server, like Venus, runs as a user-level process. Furthermore, trustworthy Vice machines are permitted to operate an authentication server. Lastly, update processes are utilised to ensure that meta data on the file system is consistent throughout all Vice servers.
- 14. CODA presents to users as a standard UNIX-based file system. It supports the vast majority of the operations defined in the VFS specification.
- 15. In contrast to NFS, CODA provides a globally shared name space that is managed by the Vice servers. This namespace is accessible to clients via a specific subdirectory in their local namespace.
- 16. Whenever a client looks up a name in this subdirectory, Venus ensures that the appropriate part of the shared namespace is mounted locally.
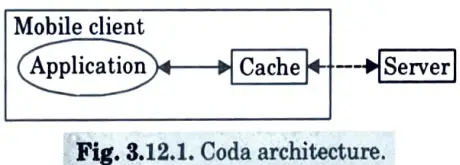


B. Disconnected operations in CODA :
- 1. Disconnected operations are a method of operation that allows a client to continue accessing vital data even while the shared data repository is temporarily unavailable.
- 2. It is a transient divergence from usual behaviour as a shared repository client.
- 3. Disconnected operation in a file system is viable, efficient, and practical.
- 4. The key premise is that data caching, which is commonly used to improve performance, may also be utilised to improve availability.
Section 6 : Fault Tolerance Issues Mobile Computing
a. Describe the Fault Tolerance issues involved in mobile computing ? What is the monitoring process ?
Ans.
- 1. The capacity of mobile agents to react dynamically to unfavourable situations and events facilitates the development of resilient and fault-tolerant distributed systems.
- 2. For example, if a host is being shut down, all agents running on that computer are notified and given enough time to dispatch and continue their operations on another host in the network.
- 3. The use of virtual machines and interpreters has enabled mobile agents to move from one platform to another in a heterogeneous environment.
- 4. However, due to differing representations in the underlying hardware, virtual machines and interpreters can only provide limited support for the preservation and resumption of the execution state in heterogeneous environments.
- 5. For example, although a number of research efforts are underway to address this issue, the full execution state of an object cannot currently be retrieved in java.
- 6. Java programmes cannot currently access information such as the status of the programme counter and the frame stack.
- 7. Despite the fact that mobile agents have a high degree of autonomy and perform well in disconnected operations, the failure of the home platform or other platforms on which the agents rely on a number of research projects, such as Nomads at the University of West Florida, are using modified Java Virtual Machines to capture the frame stack and provide security services, which can severely limit their intended functionality.
- 8. While transferring a mobile agent to another machine can make it more fault tolerant, the mobile agent’s reliance on the safe operation of a safe home or trusted platform limits its capabilities.
- 9. Designers of mobile agent platforms must also balance security and fault tolerance.
- 10. To address the security problems associated with “multi hop agent mobility,” various agent architectures have been developed on centralised client-server models that require agents to return to a central server before moving on to another host system.
- 11. Obviously, addressing security vulnerabilities in this manner exposes all mobile agents to a central server failure and introduces scalability concerns.
Monitoring process :
- 1. A prediction mechanism is built to identify critical host agents so as to prevent failure.
- 2. Therefore, updating of information in the system can be done in a consistent fashion.
- 3. In this case, the weighing computation is included, which means that the weights of the hosts are taken into account.
- 4. Mobile agents that operate as monitoring agents notice unforeseen situations and assist in their recuperation.
- 5. The host dependence calculation is further proposed by using an algorithm to update weights.
- 6. In other words, the criticality of hosts in a mobile system is calculated.
- 7. The goal is to monitor constantly, however in order to acquire trustworthy behaviour, the host agents are watched dynamically, resulting in improved system response.
- 8. Hence, proposed monitoring mechanism has the following components :
- a. Monitor Agent (MoA) :
- i. In the whole module of monitoring, these are at the lower level i.e., they reside on hosts that provide services.
- ii. These service hosts keep a record of information in the form of log tables.
- iii. These agents monitor the surrounding atmosphere and gather information of exchanging messages.
- b. Manager Agent (MaM) :
- i. This resides at the higher level and controls the agents during monitoring.
- ii. It can correlate different local events from various monitored hosts in time.
- c. Alert Agent (AlA) :
- i. It is made up of many blocks like time stamps that include the alert message creation time, threshold event detection time, alert in case of any fault and alarm information as well.
- ii. But this works under the MaM.
b. Describe the characteristics and applications of mobile agents. Why mobile agents are used ?
Ans. A. Characteristics of mobile agents :
Following are the characteristics of mobile agent :
- 1. Situatedness: It means that an agent receives sensory input from its environment and it can perform actions which change the environment in some way.
- 2. Autonomy: It means that an agent is able to act without the direct intervention of humans (or other agents) and it has control over its own actions and internal states.
- 3. Flexibility: It can be defined to include the following properties :
- a. Responsive: It refers to an agent ability to perceive its environment and respond in a timely fashion to changes that occur in it.
- b. Proactive: Agents are able to exhibit opportunistic, goal-driven behaviour and take the initiative where appropriate.
- c. Social: Agents should be able to interact, when appropriate, with other agents and human in order to solve their own problems and to help others with their activities.
- 4. Rationality: The assumption that an agent will not act in a manner that prevents it from achieving its goals.
- 5. Mobility: The ability for an agent to move across networks and between different hosts to fulfill its goal.
B. Applications of mobile agents :
- 1. Networked computer system users must meet four major security requirements: confidentiality, integrity, accountability, and availability.
- 2. Users of agent and mobile agent frameworks face the same security challenges.
- 3. This section provides a brief overview of these security requirements and how they apply to agent frameworks:
- a. Confidentiality :
- i. All private information stored on a platform or conveyed by an agent must be kept private.
- ii. Agent frameworks must be able to ensure the confidentiality of intra- and inter-platform communications.
- iii. Eavesdroppers can learn about an agent’s activity not only from the content of messages transmitted, but also from the message flow from one agent to another or agents.
- b. Integrity :
- i. The agent platform must safeguard agents against unauthorised changes to their code, state, and data, and it must ensure that only authorised agents or processes modify shared data.
- ii. While the agent cannot prevent a malicious agent platform from interfering with its code, state, and data, it can take steps to identify such tampering.
- c. Accountability :
- i. On a particular platform, each process, human user, or agent must be held accountable for their actions.
- ii. Each process, human user, or agent must be uniquely identified, authenticated, and audited in order to be held accountable.
- iii. Examples of behaviours for which they must be held accountable include gaining access to an item such as a file or modifying a platform security mechanism.
- iv. Accountability necessitates the keeping of an audit log of security-related events that have happened, listing each event as well as the agent or process accountable for that occurrence.
- d. Availability :
- i. The agent platform must be capable of ensuring data and service availability to both local and remote agents.
- ii. The agent platform must offer controlled concurrency, simultaneous access, deadlock management, and exclusive access as needed.
- iii. The agent platform must be capable of detecting and resolving system software and hardware issues.
- iv. While the platform can provide some fault-tolerance and fault-recovery, agents may be forced to take responsibility for their own fault-recovery.
C. Reason :
- 1. They facilitate high quality, high performance, economical mobile applications.
- 2. Bandwidth :
- a. Distributed systems often rely on communications protocols that involve multiple interactions to accomplish a given task.
- b. This is especially true when security measures are enabled.
- c The result is a lot of network traffic.
- d. As illustrated in Fig. mobile agents enable the packaging of a conversation and dispatching it to a destination host where interactions can take place locally.
- e. Mobile agents can also help to reduce the flow of raw data in the network.
- f. When very large amounts of data are stored at remote hosts, they should be processed locally rather than sent across the network.
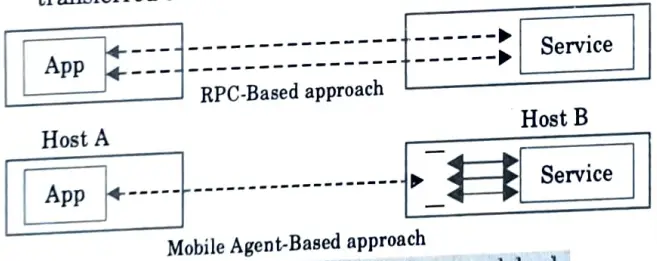


- g. The motto is simple : move the computations to the data rather than the data to the computations.
- 3. Latency: By migrating to the location of the resource, a mobile agent can interact with the resource much faster than from across the network.
- 4. Asynchronous task execution
- 5. Fault tolerance
- 6. They enable use of portable, low cost personal communications.
- 7. Peer to peer communication
- 8. They permit secure intranet style communications on public networks.
Section 7 : MANET in Mobile Computing
a. Discuss the DSDV with example and differentiate it from AODV. Explain proactive, reactive routing protocol.
Ans. A. DSDV: The DSDV routing algorithm is an extension of the Bellman-Ford routing method. C. Perkins created this routing protocol in 1994, and it is a proactive distance vector routing technology. This protocol ensures that there are no loops.
In DSDV :
- 1. Each node keeps a routing database that contains information about all possible routes in a network, the number of hops in each route, and the node sequence.
- 2. The sequence number assigned by the route’s destination node indicates how old the route is. The route is older if the sequence number is lower. When node A wants to find a path to node B, it consults its routing database. If more than one such route is discovered, the newest one is selected, and if multiple routes have the same sequence number, the shortest route is picked.
- 3. To transmit topological knowledge throughout the network, network nodes broadcast their routing tables on a regular basis. Aside from this periodic transmission, a station (node) also communicates its routing table if the topology changes significantly.
- 4. The propagation of routing table’s results in large overhead. To solve this problem, two types of updates are defined :
- a. Full dump update
- b. Incremental update
- 5. During a full dump update, stations (nodes) send the entire routing table. Because the routing database is so extensive, a full update usually entails more than one packet broadcast.
- 6. Incremental updates are sent between full dumps and contain only the information carried in a single packet. After updating, the transmitter assigns a unique sequence number. Whole dumps are rarely utilised in a network with a slowly changing topology since incremental dumps can express the gradual topology changes.
B. Difference:
| S. No. | AODC | DSDV |
| 1. | Table required before pre communication routing information. | No table is required before communication. |
| 2. | Constant and periodic propagation of route maintenance packet is required. | No periodic update is required. |
| 3. | More power consumption. | Less power consumption. |
| 4. | Less efficient. | More efficient. |
| 5. | Substantial traffic in route network due to packet flood. | Less traffic to the route map. |
| 6. | Less latency. | More latency. |
C. Pro-active and reactive routing protocol :
- 1. In a table-driven routing system, each node keeps one or more tables with routing information for each other node in the network.
- 2. To maintain a consistent and up-to-date view of the network, all nodes update their tables.
- 3. As the network topology changes, the node sends an update message throughout the network to keep the routing information consistent and up to date for the entire network.
- 4. The adhoc protocols, that follows the proactive routing protocol are as follows :
- i. Destination Sequence Distance Vector Routing Protocol (DSDV)
- ii. Wireless Routing Protocol (WRP)
- iii. Global State Routing (GSR)
- iv. Fisheye State Routing (FSR)
- v. Hierarchical State Routing (HSR)
- vi. Zone-based Hierarchical Link State Routing
- vii. Clusterhead Gateway Switched Routing (CGSR)
b. What are the characteristics of MANET? Explain the process of path discovery and path maintenance in DSR routing protocols.
Ans. Characteristic of Manet :
The process of path discovery and path maintenance in DSR routing protocols are as follows :
1. Route discovery :
- a. Route discovery allows every host in the adhoc network to dynamically discover the path to any destination.
- b. When a source node wishes to transmit a packet to a destination, it checks its route cache to see if a route to the destination already exists.
- c. If it discovers an unexpired path to the target, it uses that route to send the packet.
- d. If it does not have a valid route, it broadcasts a route request packet to its neighbours.
- e. The route request (RREQ) packet contains the source address, request id and a route record in which the sequence of hops traversed by the request packet before reaching the destination are noted down as shown in Fig.
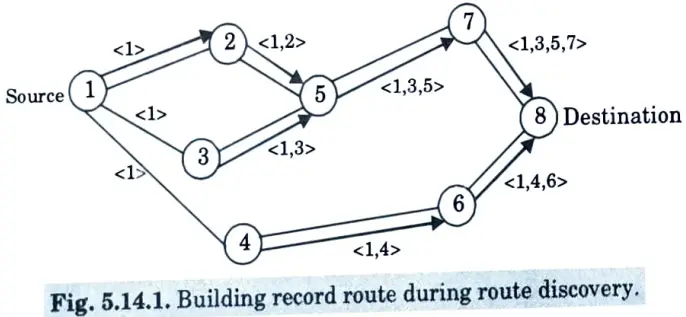


- f. Each intermediate node determines if it is aware of a route to the destination.
- g. It does not append its address to the packet’s route record and instead passes the packet to its neighbours.
- h. To reduce the number of route requests propagated, a node processes the route request packet only if it has not seen it before and its address is not present in the packet’s route record.
- i. A route reply (RREP) is generated when the route request packet is received by either the destination or an intermediate node with current information about the destination.
- j. If the destination generates the route reply, it inserts the route record from the route request packet into the route reply packet.
- k. On the other hand, if the node generating the route reply is an intermediate node then it appends its cached route to destination to the route record of route request packet and puts that into the route reply packet as shown in Fig.
- l. To send the route reply packet, the responding node must have a route to the source. If it has a route to the source in its route cache, it can use that route.
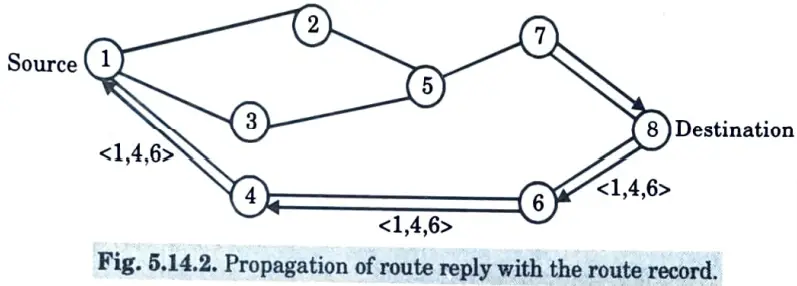


2. Route maintenance :
- a. Route maintenance is the procedure of monitoring the correct operation of route in use.
- b. The host that uses the route does this maintenance.
- c. DSR uses two type of packets for route maintenance :
- i. Route error packet
- ii. Acknowledgements
- d. A Routing Error Packet is generated when a node experiences a fatal transmission error at the data connection layer (RERR).
- e. When a node receives a route error packet, it deletes the incorrect hop from its routing cache.
- f. At that point, any routes that contain the incorrect hop are trimmed. Acknowledgement packets are used to ensure that the route links are working properly.
- g. Passive acknowledgements occur when a node hears the next hop passing the packet along the route.

2 thoughts on “Mobile Computing: AKTU Question Paper with Answer”