AKTU B.Tech’s Computer System Security exam is a crucial exam for students pursuing the discipline. It is essential to have a solid knowledge of essential topics, such as computer network security, encryption, and access control, in order to pass the exam. The last year’s question paper from 2023 is a useful resource for students preparing for the test.
Section A: Short Questions of Computer System Security
a. Why is session hijacking successful?
Ans. One of the most valuable byproducts of this type of attack is the ability to gain access to a server without having to authenticate to it. Once the attacker hijacks a session, they no longer have to worry about authenticating to the server as long as the communication session remains active.
b. What is the significance of confinement principle?
Ans. Significance of confinement principle are :
- 1. Easier to maintain and update.
- 2. Greater consistency in design.
- 3. More formatting options.
- 4. Lightweight code.
c. How access control in UNIX is different from Windows?
Ans. UNIX is a command-based OS. In contrast, Windows is a menu- based OS. UNIX is fully case-sensitive, and files can be considered separate files. In contrast, Windows has case sensitivity as an option.
d. How many look-up zones are in DNS ?
Ans. There are two Primary zone types that can be set up on a DNS Server-Forward Lookup Zones and Reverse Lookup Zones.
e. Define firewall and its uses ?
Ans. Firewall: firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted network and an untrusted network, such as the Internet.
Uses: Firewalls provide protection against outside cyber attackers by shielding your computer or network from malicious or unnecessary network traffic. Firewalls can also prevent malicious software from accessing a computer or network via the internet.
Section B: Long Question of Computer System Security
a. What is control hijacking with an example? Explain the term of buffer overflow in control hijacking.
Ans.
- 1. Hijacking is a type of network security attack in which the attacker takes control of a communication.
- 2. In hijacking (also known as a man in the middle attack), the perpetrator takes control of an established connection while it is in progress.
- 3. The attacker intercepts messages in a public key exchange and then retransmits them, substituting their own public key for the requested one, so that the two original parties still appear to be communicating with each other directly.
- 4. The attacker uses a program that appears to be the server to the client and appears to be the client to the server. This attack may be used simply to gain access to the messages, or to enable the attacker to modify them before retransmitting them.
- 5. Attacker’s goal in control hijacking:
- a. Takeover target machine (for example web server)
- b. Execute arbitrary code on target by hijacking application control flow
- 6. There are three types of control hijacking in computer security:
- a. Buffer overflow attacks
- b. Integer overflow attacks
- c. Format string vulnerabilities
Buffer overflow in Control Hijacking:
- 1. Buffers are memory storage regions that temporarily hold data while it is being transferred from one location to another.
- 2. A buffer overflow (or buffer overrun) occurs when the volume of data exceeds the storage capacity of the memory buffer.
- 3. As a result, the program attempting to write the data to the buffer overwrites adjacent memory locations.
- 4. Attackers exploit buffer overflow issues by overwriting the memory of an application. This changes the execution path of the program, triggering a response that damages files or exposes private information.
- 5. Following are the types of buffer overflow attacks:
- a. Stack-based buffer overflows: These are more common, and leverage stack memory that only exists during the execution time of a function.
- b. Heap-based attacks: These are harder to carry out and involve flooding the memory space allocated for a program beyond memory used for current runtime operations.
b. Write short notes on system call interposition.
Ans.
- 1. System call interposition is a powerful technique for regulating and monitoring program behaviors.
- 2. It enables security systems to monitor all of the application’s interaction with network, file system and other sensitive system resources.
- 3. Many security systems use system call interposition to detect anomalous program behaviors.
- 4. The discrimination between normal and abnormal behavior is based on what system calls are normally invoked by a running program.
- 5. To guarantee the effectiveness and security of these security systems, system calls must be intercepted and handled safely and completely.
- 6. However, in traditional system call interposition techniques are usually implemented in operating system kernel.
- 7. Thus they are vulnerable to kernel attacks.
- 8. To overcome this we use a virtual machine monitor (VMM)-based system call interposition approach which cannot be bypassed even if the kernel has been comprised.
c. What is cross site scripting? How to protect against XSS attacks.
Ans. Cross-Site Scripting (XSS):
- a. Injects malicious code from a trusted source to execute scripts in the victim’s browser that can hijack user sessions or redirect the user to malicious sites.
- b. Cross-site scripting is a common vector that inserts malicious code into a web application found to be vulnerable.
- c. Unlike other web attack types, such as SQL, its objective is not our web application. Rather, it targets its users, resulting in harm to our clients and the reputation of our organization.
To protect against XSS attacks:
- a. The first method used to prevent XSS vulnerabilities from appearing in our applications is by escaping user input.
- b. Escaping data means taking the data an application has received and ensuring it is secure before rendering it for the end user.
- c. By escaping user input, key characters in the data received by a web page will be prevented from being interpreted in any malicious way.
- d. In essence, we are censoring the data our web page receives in a way that will disallow the characters especially <and> characters from being rendered, which otherwise could cause harm to the application and/or users.
d. Explain the term public key cryptography in detail.
Ans.
- 1. In public key cryptography, there are two keys: a private key and a public key.
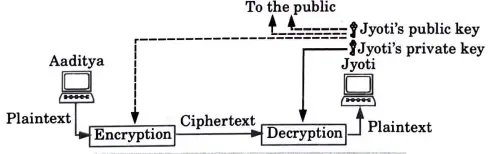
- 2. The private key is kept by the receiver. The public key is announced to the public.
- 3. In Fig. 4.1.1 imagine Aaditya wants to send a message to Jyoti. Aaditya uses the public key to encrypt the message. When the message is received by Jyoti, the private key is used to decrypt the message.
- 4. In public key encryption/decryption, the public key that is used for encryption is different from the private key that is used for decryption.


e. Explain in brief about RSA public key cryptography.
Ans. 1. RSA is a public key encryption algorithm, named for its inventors (Rivest, Shamir and Adleman).
2. The RSA algorithm is based on the mathematical part that it is easy to find and multiply large prime numbers together, but it is extremely difficult to factor their product.
3. The RSA algorithm is shown as:
a. Choose two large prime numbers p and q.
b. Calculate n = p x q.
c. Select the public key (i.e., the encryption key) e such that it is not a factor of (p-1) and (q − 1).
d. Select the private key (i.e., the decryption key) d such that the following equation is true:
(d x e) mod (p-1) x (q – 1) = 1
e. For encryption, calculate the cipher text C from the plain text M as follows:
C = Me mod n
f. Send C as the cipher text to the receiver.
g. For decryption, calculate the plain text C from the cipher text C as follows:
M = Cd mod n
Section 3: Important Questions in Computer System Security
a. How security system should evolve to handle cyber security threats and vulnerabilities?
Ans. 1. A security system should identify, classify, remedy, and mitigate the security threats and vulnerabilities.
2. To handle cyber security threats and vulnerabilities a security system must incorporate advanced security strategies.
3. A security system should evolve by incorporating following advanced security strategies to handle cyber security threats and vulnerabilities:
- A. Threat prevention strategies:
- 1. Security researchers are researching and innovating effective solutions to prevent threats.
- 2. They work around the clock aiming at zero-day vulnerabilities and are also actively involved in conducting awareness programs.
- 3. Threat prevention strategies are mainly categorized into four main sections. They are as follows:
- i. Reduce the attack surface: Continuous process of vulnerability scanning practice helps to determine top risk applications, security gaps in the network, risky users and processes, and more.
- ii. Complete visibility: End-point security can be compromised by using SMB-based vulnerior from So, it is important to separate normal SMB behavior from strange SMB behaviors, and this categorization can be done by providing complete visibility. to prevent,
- iii. Prevent known threats: Firewalls and anti-virus software are necessary threats. It is the first step towards defending networks and endpoints.
- iv. Prevent unknown threats: Advanced and unknown threats are evolving as never before. To deal with such threats, organizations have to adopt new techniques such as dynamic and behavioral analysis, deep learning techniques, and attacker techniques, tactics, and procedures (TTPs) analysis.
- B. Zero-trust approach:
- 1. The Zero-trust approach strategy is the continuous verification of all data and assets.
- 2. It helps to detect the attackers who withdraw sensitive information through lateral movements.
- 3. Following is the process of the Zero-trust approach:
- i. Identify and classify sensitive data
- ii. Map the data flow
- iii. Architect the network
- iv. Create the policy base
- v. Continuous monitoring
- C. Assume breach approach:
- 1. It is a way of testing the incident response force of an organization.
- 2. It provides various security solutions and services. They are as follows:
- i. Red-team exercise: It is an advanced version of penetration testing, where a team of highly professional security experts not only finds vulnerabilities but also tests an organization’s threat detection and response capabilities.
- ii. Continuous monitoring: Continuous monitoring is necessary to detect threats at an early stage, and it can be achieved by providing real-time visibility of users as well as network endpoints. An active security monitoring system can ensure cyber hygiene and compliance by actively monitoring the network, application, and user activities.
b. What is a digital signature? How digital signature works?
Ans. 1. Digital signature is a mathematical scheme used for verifying the authenticity of digital message or documents.
2. Digital signature uses three algorithms:
- a. Key generation: This algorithm selects a private key uniformly at random from a set of possible private keys. Output of this algorithm is private key and its corresponding public key.
- b. Signing algorithm: It produce signature by using message and private key.
- c. Signature verifying algorithm: For a given message, signature and public key, either accepts or rejects the messages claim to authenticity.
3. Fig. 4.11.1 shows the concept of digital signature.
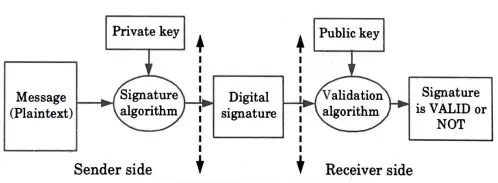


The steps followed in creating digital signature are:
- 1. Message digest is computed by applying hash function on the message and then message digest is encrypted using private key of sender to form the digital signature.
- 2. Digital signature is then transmitted with the message.
- 3. Receiver decrypts the digital signature using the public key of sender.
- 4. The receiver now has the message digest.
- 5. The receiver can compute the message digest from the message.
- 6. The message digest computed by receiver and the message digest got by decryption needs to be same for ensuring integrity.
Section 4: Important Questions in Computer System Security
a. How to detect rootkits? Explain in how to prevent rootkits?
Ans. Rootkits can be detected using detection methods which include:
a. Behavioural-based methods
b. Signature scanning
c. Memory dump analysis
Following are the method to prevent rootkits :
- 1. Avoid opening suspicious emails :
- a. Statistics shows that malware, including rootkits, are distributed through emails.
- b. This means that the chances of getting infected with a rootkit via email are high.
- c. Using another type of malware, hackers collect email addresses on the internet, which they flood with spam emails.
- d. The rootkit installs silently in the background when the user opens the infected email.
- e. To prevent rootkits from infiltrating our computer, avoid opening suspicious emails, especially if the sender is unfamiliar to us.
- 2. Avoid downloading cracked software:
- a. Cracked software may be free but it is also unsafe.
- b. Cracked software is commonly used by hackers to install rootkits on victims’ computers.
- c. Cracked software is sometimes bundled with Adware (a software), which generates stubborn and annoying pop-ups on the computer.
- d. To prevent rootkits and other types of malware, download legitimate software only.
- 3. Install software updates:
- a. Through system vulnerabilities, a rootkit can get through to our computer.
- b. System vulnerabilities are inevitable. In fact, programmers are often only able to discover a bug after the software is released. The solution is a software update.
- c. Unfortunately, some users ignore the importance of software updates. But the fact is that installing software updates enhances our cyber security, preventing malware like rootkits from getting onto our computer.
- d. When software updates become available, do not delay their installation.
- 4. Anti-malware software with rootkit detection:
- a. Anti-malware software prevents varieties of malware. But advanced anti-malware software with rootkit detection is required to stop rootkits from getting on the computer.
- b. Anti-malware software equipped with a Host Intrusion Prevention System as a feature is specifically designed to monitor computer
- c. memory. It prevents any malicious software from loading on the kernel of the operating system, which prevent rootkits using anti-malware software.
b. Explain the need of software fault isolation.
Ans.
- 1. When protecting a computer system, it is often necessary to isolate an untrusted component into a separate protection domain and provide only controlled interaction between the domain and the rest of the system.
- 2. Complex systems usually contain boundaries to prevent errors in one part propagating to other parts, which is a basic software fault-tolerance technique.
- 3. Software Fault Isolation (SFI) is a security-enhancing program transformation for instrumenting an untrusted binary module so that it runs inside a dedicated isolated address space.
- 4. Compared to other isolation mechanisms, it enjoys the benefits of high efficiency, being readily applicable to legacy native code, and not relying on special hardware or OS support.
- 5. SFI has been successfully applied in many applications, including isolating OS kernel extensions, isolating plug-ins in browsers, and isolating native libraries in the Java Virtual Machine.
Section 5: Important Questions in Computer System Security
a. How cross site request forgery attack works? Also mention example of CSRF attack.
Ans.
- 1. Cross-site request forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they are currently authenticated.
- 2. CSRF attacks specifically target state-changing requests, not theft of data, since the attacker has no way to see the response to the forged request.
- 3. With the help of social engineering (such as sending a link via email or chat), an attacker may trick the users of a web application into executing actions of the attacker’s choosing.
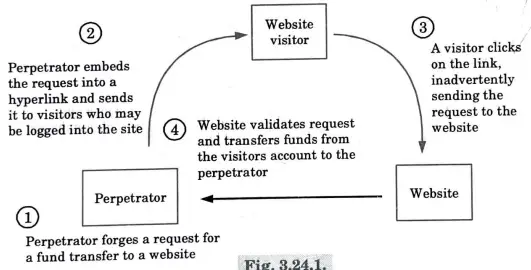


- 4. If the victim is a normal user, a successful CSRF attack can force the user to perform state changing requests like transferring funds, changing their email address, and so forth.
- 5. If the victim is an administrative account, CSRF can compromise the entire web application.
- 6. Cross-Site Request Forgery (CSRF) is an attack vector that tricks a web browser into executing an unwanted action in an application to which a user is logged in.
- 7. A successful CSRF attack can be devastating for both the business and user. It can result in damaged client relationships, unauthorized fund transfers, changed passwords and data theft-including stolen session cookies.
- 8. As the unsuspecting user is authenticated by their application at the time of the attack, it is impossible to distinguish a legitimate request from a forged one.
b. What’s the difference between browser isolation and remote browser isolation?
Ans.
| S. No. | Browser isolation | Remote browser isolation |
| 1. | Browser isolation is a cyber security model which aims to physically isolate an internet user’s browsing activity away from their local networks and infrastructure. | When a browser isolation technology is delivered to its customers as a cloud hosted service, this known as remote browser isolation (RBI). |
| 2. | It is hosted as part of an organization’s internal IT environment. | It is separate from an organization’s internal IT environment. |
| 3. | It requires more client-side resources. | It requires lesser client-side resources. |
| 4. | Latency is low. | Latency is high. |
| 5. | Low bandwidth consumption. | High bandwidth consumption. |
Section 6: Important Questions in Computer System Security
a. Explain RSA algorithm. Perform encryption and decryption using RSA for p = 11, q = 13, e = 7, m = 9.
Ans. RSA algorithm :
1. RSA is a public key encryption algorithm, named for its inventors (Rivest, Shamir and Adleman).
2. The RSA algorithm is based on the mathematical part that it is easy to find and multiply large prime numbers together, but it is extremely difficult to factor their product.
3. The RSA algorithm is shown as:
a. Choose two large prime numbers p and q.
b. Calculate n = p x q.
c. Select the public key (i.e., the encryption key) e such that it is not a factor of (p-1) and (q − 1).
d. Select the private key (i.e., the decryption key) d such that the following equation is true:
(d x e) mod (p-1) x (q – 1) = 1
e. For encryption, calculate the cipher text C from the plain text M as follows:
C = Me mod n
f. Send C as the cipher text to the receiver.
g. For decryption, calculate the plain text C from the cipher text C as follows:
M = Cd mod n
Numerical:
Step 1: p = 11, q = 13.
Step 2: n = px q = 11 x 13 = 143
Step 3: Calculate
ɸ(n) = (p-1) (q − 1)
= (11-1) (13-1)= 10 x 12 = 120
Step 4: Determine d such that de= 1 (mod 160)
d = e-1 mod 160
Using extended Euclidean algorithm we calculate d.
| q | r1 | r2 | r | t1 | t2 | t |
| 17 7 | 120 7 1 | 7 1 0 | 1 0 | 0 1 -17 | 1 -17 120 | -17 120 |
= – 17 mod 120
d = 103
Public key = {7, 143)
Private key = {103, 143}
Encryption (C) = Me (mod n)
M = 9
C = 97 mod 143
= [(94 mod 143) x (92 mod 143)
= (91 mod 143)]mod 143
= (126 × 81 × 9) mod 143
= 91854 mod 143 = 48
Decryption (M) = 13103 mod 143
b. What is symmetric and asymmetric key cryptography? Write their respective advantages and disadvantages?
Ans.
| S. No. | Symmetric-key cryptography | Asymmetric-key cryptography |
| 1. | It uses a single key for both encryption and decryption of data. | It uses two different keys-public key for encryption and private key for decryption. |
| 2. | Both the communicating parties share the same algorithm and the key. | Both the communicating parties should have at least one of the matched pair of keys. |
| 3. | The processes of encryption and decryption are very fast. | The encryption and decryption processes are slower as compared to symmetric-key cryptography. |
| 4. | Key distribution is a problem. | Key distribution is not a problem. |
| 5. | The size of encrypted text is same or less than the original text. | The size of encrypted text is more than the size of the original text. |
- 1. Simple: This type of encryption is easy to carry out. All users have to do is specify and share the secret key and then begin to encrypt and decrypt messages.
- 2. Encrypt and decrypt your own files: If you use encryption for messages or files which you alone intend to access, there is no need to create different keys. Single-key encryption is best for I this.
- 3. Fast: Symmetric key encryption is much faster than asymmetric key encryption.
- 4. Uses less computer resources: Single-key encryption does not require a lot of computer resources when compared to public key encryption.
- 5. Prevents widespread message security compromise: A different secret key is used for communication with every different party. If a key is compromised, only the messages between a particular pair of sender and receiver are affected. Communications with other people are still secure.
Disadvantages of symmetric key cryptography:
- 1. Need for secure channel for secret key exchange: Sharing the secret key in the beginning is a problem in symmetric key encryption. It has to be exchanged in a way that ensures it remains secret.
- 2. Too many keys: A new shared key has to be generated for communication with every different party. This creates a problem with managing and ensuring the security of all these keys.
- 3. Origin and authenticity of message cannot be guaranteed: Since both sender and receiver use the same key, messages cannot be verified to have come from a particular user. This may be a problem if there is a dispute.
Advantages of asymmetric key cryptography:
- 1. The key distribution problem is eliminated because there’s no need for exchanging keys.
- 2. Security is increased since the private keys don’t ever have to be transmitted or revealed to anyone.
- 3. The use of digital signatures is enabled so that a recipient can verify that a message comes from a particular sender.
- 4. It allows for non-repudiation, so the sender can’t deny sending a message.
Disadvantages of asymmetric cryptography include:
- 1. It’s a slow process compared to symmetric cryptography. Therefore, it’s not appropriate for decrypting bulk messages.
- 2. If an individual loses his private key, he can’t decrypt the messages he receives.
- 3. Because public keys aren’t authenticated, no one can ensure a public key belongs to the person specified. Consequently, users must verify that their public keys belong to them.
Section 7: Important Questions in Computer System Security
a. How do you define risk, vulnerability and threat in the context of network security?
Ans.
| S.No. | Threat | Vulnerability | Risks |
| 1. | Take advantage of vulnerabilities in the system and have the potential to steal and damage data. | Known as the in weakness hardware, software, or designs, which might allow cyber threats to happen. | The potential for loss or destruction of data is caused by cyber threats. |
| 2. | Generally, can’t be Controlled. | Can be controlled. | Can be controlled. |
| 3. | It may or may not be intentional. | Generally, unintentional. | Always intentional. |
| 4. | Can be blocked by Managing the vulnerabilities. | Vulnerability management is a process of identifying the problems, then categorizing them, prioritizing them, and resolving the vulnerabilities in that order. | Reducing data transfers, downloading files from reliable sources, updating the software regularly, hiring a professional cyber security team to monitor data, developing an incident management plan, etc., help to lower down the possibility of cyber risks. |
| 5. | Can be detected by antivirus software and threat detection logs. | Can be detected by testing hardware and many vulnerability scanners. | Can be detected by identifying mysterious emails, suspicious pop- ups, observing unusual password activities, a slower than normal network, etc. |
b. What is a network intrusion detection system? Explain its types.
Ans. Network Intrusion Detection System (NIDS):
- a. It is an independent platform that identifies intrusions by examining network traffic and monitors multiple hosts.
- b. It gains access to network traffic by connecting to a network hub, a network switch configured for port mirroring, or a network tap.
- c. In a NIDS, sensors are placed at choke points in the network to monitor, often in the Demilitarized Zone (DMZ) or at network borders.
- d. Sensors capture all network traffic and analyze the content of individual packets for malicious traffic.
- e. An example of a NIDS is Snort.
Types of network intrusion detection system: Intrusion detection systems (IDS) are classified into 5 types:
- A. Network Intrusion Detection System (NIDS):
- 1. NIDS are set up at a planned point within the network to examine traffic from all devices on the network.
- 2. It performs an observation of passing traffic on the entire subnet and matches the traffic that is passed on the subnets to the collection of known attacks.
- 3. Once an attack is identified or abnormal behavior is observed, the alert can be sent to the administrator.
- B. Host Intrusion Detection System (HIDS) :
- 1. HIDS run on independent hosts or devices on the network.
- 2. A HIDS monitors the incoming and outgoing packets from the device only and will alert the administrator if suspicious or malicious activity is detected.
- C. Protocol-based Intrusion Detection System (PIDS):
- 1. PIDS comprises a system or agent that would consistently resides at the front end of a server, controlling and interpreting the protocol between a user/device and the server.
- 2. It secures the web server by regularly monitoring the HTTPS protocol stream and accepting the related HTTP protocol.
- D. Application Protocol-based Intrusion Detection System (APIDS):
- 1. APIDS is a system or agent that generally resides within a group of servers.
- 2. It identifies the intrusions by monitoring and interpreting the communication on application-specific protocols.
- E. Hybrid Intrusion Detection System :
- 1. Hybrid intrusion detection system is made by the combination of two or more approaches of the intrusion detection system.
- 2. In the hybrid intrusion detection system, host agent or system data is combined with network information to develop a complete view of the network system.
- 3. Hybrid intrusion detection system is more effective in comparison to the other intrusion detection system.

Good
Thanks Abhishek jagtap,
We are working on it