Access information on Computer Network Security from BCA solved exam papers. Discover the fundamentals of network security and cryptography, and obtain insightful knowledge to properly secure digital information.
Dudes 🤔.. You want more useful details regarding this subject. Please keep in mind this as well. Important Questions For Computer Network Security: * Important Short Questions * Solved Question Paper * Syllabus
Section A: Computer Network Security Very Short Question Answers
Q1. Explain various attacks.
Ans. Passive and active security assaults can be distinguished. A passive attack aims to learn or use information from the system while having no effect on system resources. An active attack aims to change or disrupt system resources.
- 1. Passive Attacks : Passive assaults are similar to eavesdropping or monitoring transmission. The opponent’s purpose is to obtain information that is being transmitted. Passive attacks do not entail any changes to the original message’s content. Passive attacks may analyse traffic to determine the type of communication taking place, or they may expose the contents of the message to someone other than the intended recipient of the message.
- 2. Active Attacks : Active assaults entail some kind of data stream alteration or the production of a bogus stream. Active attacks are the polar opposite of passive attacks. Because of the large range of potential physical and network vulnerabilities, it is extremely difficult to completely eliminate active attacks. The purpose of active defence is to detect and recover from any disruptions or delays induced by them.
Q2. What is firewall? How does it work?
Ans. A firewall is a software programme that filters information entering your computer via an internet connection. If the filters classify the data as’suspicious,’ it will be rejected. You may typically select the degree of filter, but keep in mind that if you set it too high, certain information will be unavailable.
A firewall only accepts incoming traffic that has been configured to receive it. It distinguishes between legitimate and malicious traffic and allows or blocks particular data packets based on predefined security rules. These criteria are based on numerous factors of the packet data, such as its source, destination, and content, among others. To prevent cyber attacks, they block traffic from suspected sources.
Q3. Name four factors needed for secured networks.
Ans. The four factors needed for a secure network are given below:
- (a) Privacy: The sender and the receiver expect confidentiality.
- (b) Authentication: The receiver is sure of the sender’s identity and that an imposter has not sent the message.
- (c) Integrity: The data must arrive at the receiver exactly as it.
- (d) Non-reputation: The receiver must be able to prove that a received message came from a specific sender.
Q4. Define SSL.
Ans. SSL is intended to utilise TCP to provide dependable end-to-end secure services. SSL has two layers of protocols rather than a single protocol.
The SSL record protocol provides fundamental security services to a variety of higher-layer protocols. The Hypertext Transfer Protocol (HTTP), which offers the transfer service for web client/server interaction, in particular, can work on top of SSL. SSL defines three higher-layer protocols: the handshake protocol, the change cypher standard protocol, and the alert protocol.
Q5. Write about electronic mail security.
Ans. Email security is the process of assuring the availability, integrity, and authenticity of email communications by defending against email threats. Email allows billions of people and businesses to communicate and send messages to one another.
Section B: Computer Network Security Short Question Answers
Q6. How authentication is achieved in PGP?
Ans. Authentication is defined as the process of validating something as true or actual. When we login to some websites, we occasionally provide our account name and password as part of the authentication verification process.
In the email world, checking the authenticity of an email is nothing but to check whether it actually came from the person it says. In emails, authentication has to be checked as there are some people who spoof the emails or some spams and sometimes it can cause a lot of inconvenience. The Authentication service in PGP is provided as follows:
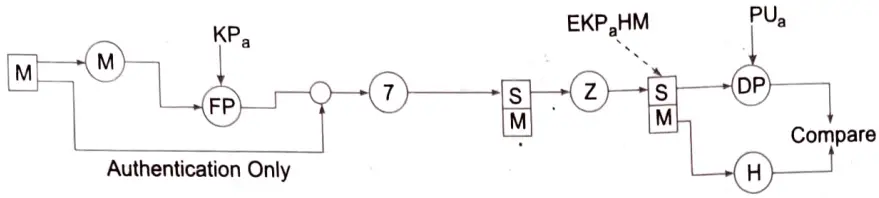


As shown in the above figure, the Hash Function (H) calculates the Hash value of the message. For the hashing purpose, SHA-1 is used and it produces a 160 bit output hash value. Then, using the sender’s private key (KPa), it is encrypted and it’s called as Digital Signature. The Message is then appended to the SIgnature. All the process happened till now, is sometimes described as signing the message. Then the message is compressed to reduce the transmission overhead and is sent over to the receiver.
The data is decompressed at the receiver’s end, and the message and signature are obtained. The signature is subsequently decoded with the sender’s public key (PUa) to retrieve the hash value. The message is handed back to the hash function, and the hash value is calculated and returned.
Both the values from the signature and the most recent output of the hash function are compared, and if they are the same, it signifies that the email was sent from a known source and is legitimate; otherwise, it is not.
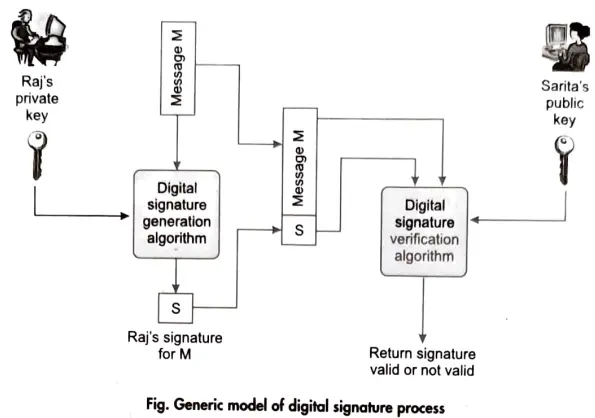
Q7. Discuss the digital signature with a neat diagram.
Ans. Digital Signature: A digital signature is an authentication mechanism that allows a message’s sender to attach a code that serves as a signature. This signature is created by hashing the message and encrypting it with the sender’s private key.
Asymmetric cryptography is a sort of digital signature system. Digital signatures utilise public key cryptography, which consists of two keys: private and public. The digital signature scheme typically consists of three algorithms:
- 1. Key Generation Algorithm: The algorithm outputs private key and a corresponding public key.
- 2. Signing Algorithm: It takes, message + private key, as input and outputs a digital signature.
- 3. Signature Verifying Algorithm: It takes, message + public key + digital signature, as input, and accepts or rejects digital signature.


Q8. Explain kerberos Authentication system.
Ans. Kerberos Authentication System : Kerberos authentication system uses a series of encrypted messages to prove to a verifier that a client is running on behalf of a particular user.
1. Kerberos Encryption: It derives and considers the user’s encryption key to be a password. The server key is an encryption key shared by each application server and the authentication server.
2. Kerberos Ticket: Initially, the client and server do not share an encryption key. When a client authenticates to a new verifier, the authentication server generates a new encryption key and securely distributes it to both parties. This new encryption key is known as a session key, and it is distributed to the verifier via the Kerberos ticket.
A Kerberos ticket is an authentication server’s certificate that has been encrypted with the server key. This ticket is not sent to the verifier directly, but rather to the client, who transmits it to the verifier as part of the application request.
3. Application Request and Response: This is the most fundamental transaction in the Kerberos protocol, in which a client verifies that it knows the session key encoded in a Kerberos ticket. When the verifier receives the application request, it decrypts the ticket, extracts the session key, and uses the session key to decrypt the authenticator. The server validates the client’s identity here. In other cases, the client also wishes to be certain of the server’s identity. In this situation, the server prepares an application response by extracting the client’s time from the authenticator and returning it to the client together with other information that has been encrypted using the session key.
4. Authentication Request and Response: Each verifier with whom the client communicates requires a distinct ticket and session key. When a client wants to associate with a specific verifier, it utilises the authentication request and response to receive a ticket and session key from the authentication server. The client includes its claimed identity, the name of the verifier, the required expiration period for the ticket, and a random number that will be used to verify the authentication response with the request in the request.
The authentication server returns the session key, the assigned expiration time, the random number from the request, the name of the verifier, and other information from the ticket as part of the application request, all encrypted with the user’s passwords registered with the authentication server.
5. Obtaining Additional Tickets: The basic Kerberos authentication protocol enables a client to receive a ticket and session key for and confirm its identity to any verifier registered with the authentication server. Each time the user authenticates with a new verifier, the user’s password must be given.
Though a Kerberos ticket and its associated key are only valid for a limited period, the user’s password can be used to get tickets and impersonate the user until the password is reset.
The Kerberos protocol’s ticket granting exchange enables a user to receive tickets and encryption keys using short-lived credentials without re-entering the user’s password.
Section C: Computer Network Security Detailed Question Answers
Q9. Explain the architecture of lP sec. Discuss Internet security association key management protocol in detail.
Ans. IP Sec Architecture
To protect traffic or data flow, IP Sec (IP Security) architecture employs two protocols. ESP (Encapsulation Security Payload) and AH (Authentication Header) are the protocols involved. Protocols, algorithms, DOl, and key management are all part of the IP sec Architecture.
Internet Security Association Key Management Protocol
The Internet Security Association and Key Management Protocol (ISAKMP) is a framework for securely creating Security Associations (SAs) and exchanging keys. SAs are agreements that govern how two devices will communicate securely. The process of transferring keys or other cryptographic material used to secure communication is referred to as key exchange.
ISAKMP is a protocol that specifies the message structure and format needed to create and maintain SAS. It makes no mention of the cryptographic techniques or keys that are employed. It instead provides a framework for negotiating these specifics and creating a secure link between two devices.
The Internet Key Exchange (lIKE) protocol, which is used to negotiate and establish SAs, is used in conjunction with ISAKMP. ISAKMP and IKE are often used to create secure Virtual Private Network (VPN) connections that enable devices to communicate securely over the internet.
The Internet Engineering Task Force (IETE) Request for Comments (RFC) 2408 defines ISAKMP. It is a key component of many Internet security protocols, and it is widely used in workplace networks and other situations where secure communication is critical.
Configuring an ISAKMP Policy
To configure an ISAKMP policy, you will need to specify the following details:
- (a) Encryption Algorithm: This is the algorithm that will be used to encrypt the data that is transmitted between the two devices. Common choices include AES (Advanced Encryption Standard) and 3DES (Triple DES).
- (b) Hash Algorithm: This is the algorithm that will be used to create a message digest or hash of the data. The hash is used to verify the integrity of the data and to ensure that it has not been tampered with. Common choices include SHA-1 (Secure Hash Algorithm 1) and SHA-2.
- (c) Authentication Method: This is the method that will be used to authenticate the devices. Options include using a identify of the devices. Options include using a shared secret (such as a password), using digital certificates, or using biometric authentication.
Diffie-Hellman Group
This is the group of mathematical values that will be used in the Diffie-Hellman key exchange algorithm. Different groups offer different levels of security with large groups providing stronger security but requiring more computation.
- (a) Lifetime: This is the amount of time that the SA will remain valid after the lifetime expires, the SA will need to be re-established.
- (b) PFS (Perfect Forward Secrecy): This is a feature that ensures that the keys used to encrypt the data not derived from previous keys. This makes it more difficult for an attacker to obtain the keys by compromising previous keys.
Q10. Describe SNMP architecture in detail. Also compare SNMP VI and SNMP V3.
Ans. SNMP Architecture
The Simple Network Management Protocol (SNMP) architecture includes four layers. As the following figure illustrates the SNMP architecture includes layers following.
(a) SNMP network managers, (b) Masters agents,
(c) Sub-agents, (d) Managed components.
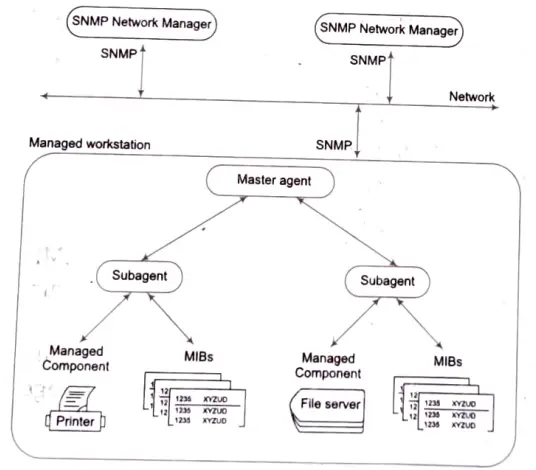


Multiple SNMP network managers can exist on the same network. One master agent can be installed on each workstation. The SNMP network administrators and master agents communicate via SNMP protocols. Each managed component is associated with a subagent and MIBs. The protocol for communication between master agents and subagents is not specified by SNMP.
SNMP VI: It is the most traditional flavour. It is simple to put up and only requires a plaintext community. The main disadvantages are that it does not handle 64 bit counters, only 32 bit counters, and has limited security. A plaintext community string delivered from a narrow range of permitted lP addresses is as secure as it gets. In other words, anyone with network access will be able to see the community string in plaintext, and faking the originating IP of a UDP packet is straightforward.
SNMP V3: Adds security to the 64 bit counters. SNMP Version 3 adds both encryption and authentication, which can be used together or separately. Setup is more complex than just defining a community string but then, what security is not? But if you require security this is the way to do it.
Q11. What do you mean by cryptography? List the various cryptographic techniques with suitable example.
Ans. Cryptography: Cryptography is the art of creating security by encoding messages in such a way that they are unreadable. It is required for sending data across a network. It aids with the protection of data in transit as well as data kept on disc.
Various Cryptographic Techniques
Cryptography is one of the key technologies utilised in the creation of a secure VPN. Different applications of the same basic algorithms can provide both encryption and authentication to ensure the two security peers in a VPN. One of two types of encryption algorithms, symmetric cryptography and asymmetric cryptography, can ensure data confidentiality.
1. Symmetric Cryptography: Symmetric cryptography, also known as conventional cryptography, requires the sender and receiver to exchange a key, which is a piece of secret information used to encrypt and decrypt data. The procedure by which two peers agree on a key over an unsecured medium can be troublesome because the peers have no way of communicating in secret until the key is agreed upon. The original unencrypted data is known as plaintext, while the encrypted form is known as ciphertext.
Symmetric cyphers use the same key to encrypt and decipher plaintext and ciphertext. As a result, the sender and recipient must agree on this key in advance, which must be unknown to anybody else. The size of the key used by a symmetric algorithm can be used to determine its cryptographic strength. DES (Data Encryption Standard), Blowfish, and AES are among examples. The DES algorithm employs a 64-bit key, with 8 bits reserved and 56 changeable bits. Instead of DES, information can be protected with 3DES (Triple DES). This means that the information is encrypted three times in a row. The use of multiple encryption cycles does not necessarily offer a concomitant increase in security and may be viewed as a waste of computing power for many applications. Blowfish allows implementers to select a key length of between 32 and 448 bits; commercially available implementations often use 128-bit keys.
Symmetric algorithms are popular because their speed enables them efficiently to encrypt large quantities of plaintext. There are two sub-categories of symmetric cipher, stream and block ciphers.
(a) Stream Ciphers: These algorithms work on a single bit at a time. A stream of plaintext enters the cypher, and an output stream of ciphertext emerges. Stream cypher encrypted messages are always the same size as the original plaintext. The encryption is accomplished through a process in which each bit of the plaintext is combined with XOR (Le. controlled by the Boolean operator exclusive OR – XOR) with a random bit to form the ciphertext. The essence of a stream cypher is the methods used to generate the stream of random bits using the shared key.
(b) Block Ciphers: Instead of encrypting data one bit at a time, these cyphers encrypt data in blocks of bytes. Block sizes vary according on the algorithm, with 64 bits being the most frequent. Because the plaintext is unlikely to be a multiple of the algorithm’s block size, padding the input is frequently required. For example, if the block length is 64 bits and the last block only includes 40 bits, 24 bits of padding must be inserted. The padding string can be made up of all zeros, alternating zeros and ones, random bits, or any other combination. Some encryption protocols require a specific padding strategy. Block cyphers include DES, Blowfish, and AES.
2. Asymmetric Cryptography: Asymmetric cryptography, often known as public key cryptography, overcomes the key exchange problem by employing two keys, either of which can be used to encrypt a message. Only the other key can then be used to decrypt the encrypted data. Messages can be received securely by posting one of the keys as a Public Key (for example, in the footer of an e-mail message) and keeping the second, the Private Key, private. Anyone desiring to send a secure communication may then encrypt the message with the recipient’s Public Key, and only the intended recipient will be able to decrypt the encrypted text and retrieve the original message if the Private Key has not been exposed.
Asymmetric cyphers have the significant advantage of not requiring a shared secret key to be exchanged across an insecure channel such as the public internet. A pair of keys is produced, with one designated as the Public Key and publicised. Anyone who wants to interact securely with the key’s owner encrypts the message with the recipient’s Public Key. The second, Private Key, which the owner assures is never released, is required for decryption.
RSA (named after its creators, Ron Rivest, Adi Shamir, and Leonard Adleman) is the most widely used asymmetric block cypher.
Q12. Draw the block diagram of DES algorithm and also explain it.
Ans. The Data Encryption Standard (DES) is a symmetric-key block cipher published by the National Institute of Standards and Technology (NIST).
DES is an implementation of a Feistel Cipher. It uses 16 round Feistel structure. The block size is 64-bit. Though, key length is 64-bit, DES has an effective key length of 56 bits, since 8 of the 64 bits of the key are not used by the encryption algorithm (function as check bits only). General Structure of DES is depicted in the following illustration:
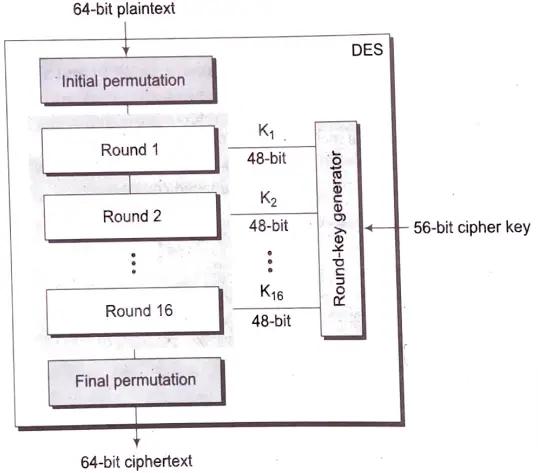


Since DES is based on the Feistel Cipher, all that is required to specify DES is:
Round function.
Key schedule.
Any additional processing-Initial and final permutation
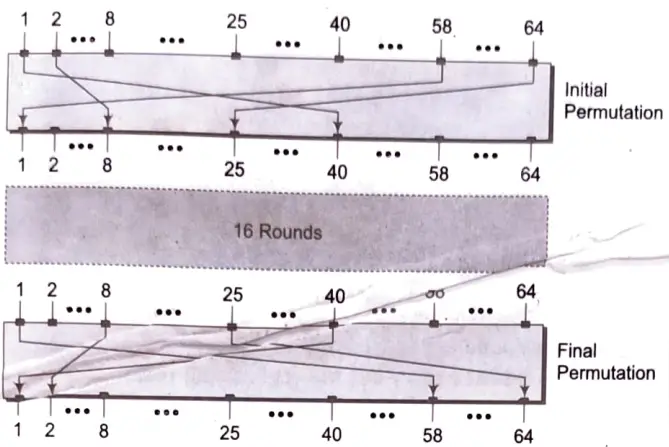
Initial and Final Permutation
The initial and final permutations are straight Permutation bOxes (P-boxes) that are inverses of each other. They have no cryptography significance in DES. The initial and final permutations are shown as.


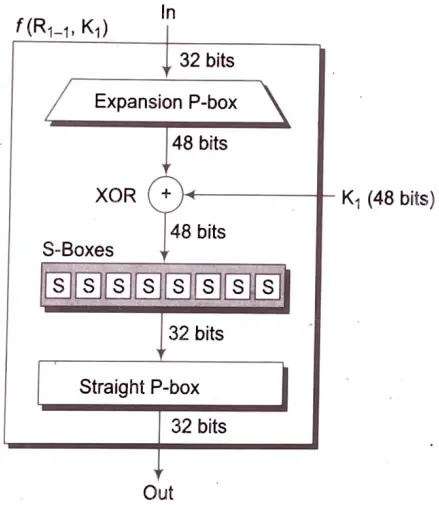
Round Function
The heart of this cipher is the DES function, f. The DES function applies a 48-bit key to the rightmost 32-bits to produce a 32-bit output.


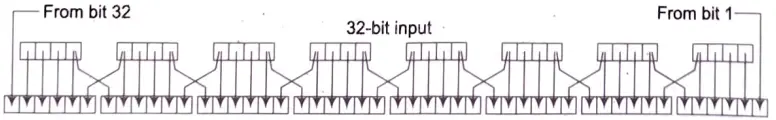
Expansion Permutation Box: Since right output is 32-bit and round key is a 48-bit, we first need to expand right input to 48-bits. Permutation logic is graphically depicted in the following illustration:


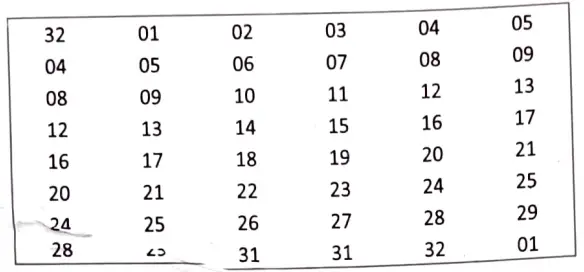
The graphically depicted permutation logic is generally described as table in DES specification illustrated as shown:


XOR (Whitener): After the expansion permutation DES does XOR operation on the expanded right section and the round key. The round key is used only in this operation.
Substitution Boxes: The S-boxes carry out the real mixing (Confusion). DES uses 8 S-boxes, each with a 6-bit input and a 4-bit output. Refer the following illustration:
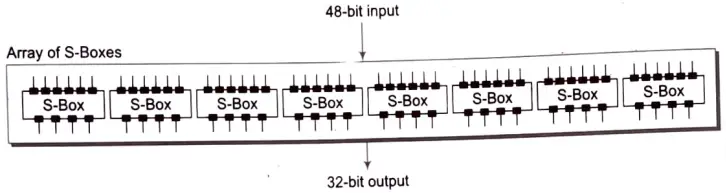


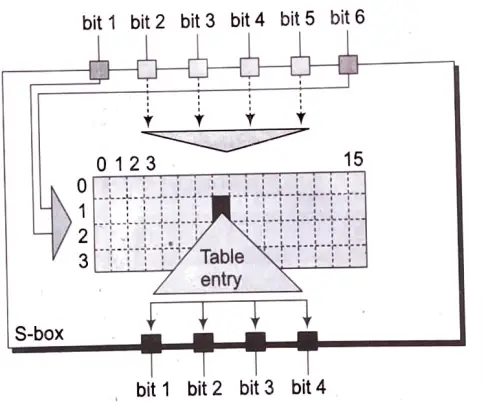


There are a total of eight S-box tables. The output of all eight s-boxes is then combined in to 32-bit section.
Straight Permutation: The 32-bit output of S-boxes is then subjected to the straight permutation with rule shown in the following illustration:
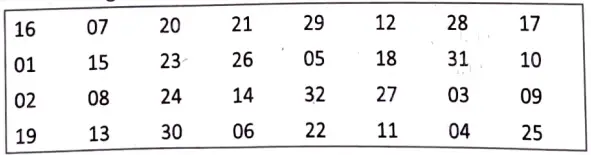


Key Generation
The. round-key generator creates sixteen 48-bit keys out of a 56-bit cipher key. The process of key generation is depicted in the following illustration:
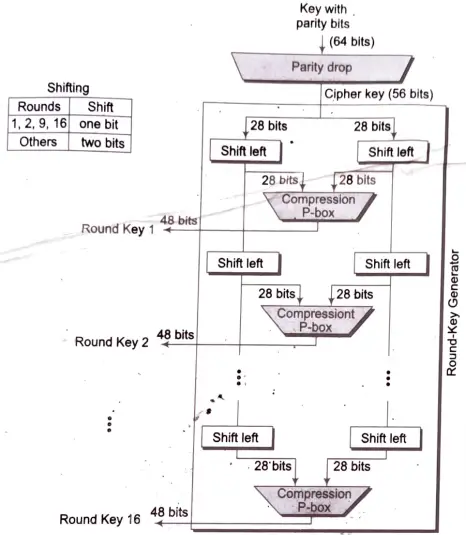


The logic for Parity drop, shifting, and compression P-box is given in the DES description.
DES Analysis
The DES satisfies both the desired properties of block cipher. These two properties make cipher very strong.
Avalanche Effect: A small change in plaintext results in the very great change in the ciphertext.
Completeness: Each bit of ciphertext depends on many bits of plaintext.
During the last few years, cryptanalysis have found some weaknesses in DES when key selected are weak keys. These keys shall be avoided.
DES has proved to be a very well designed block cipher. There have been no significant cryptanalytic attacks on DES other than exhaustive key search.
13. Write the short notes on any three.
(i) SET
Ans. SET: SET is a mechanism and electronic protocol that ensures the integrity and security of internet transactions. This early protocol was used by e-commerce companies to safeguard electronic payments made using debit and credit cards
(ii) Cryptanalysis
Ans. Cryptanalysis: Cryptanalysis is the study of recovering the plaintext when the key is not available. It is the study and practise of analysing cryptographic systems in order to comprehend how they function and how they might be cracked. By eavesdropping on an insecure channel, a cryptanalyst attempts to obtain the plaintext or decryption function of a cryptosystem.
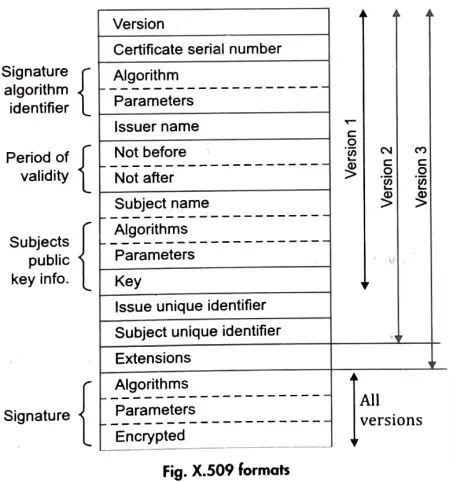
(iii) X.509 Certificate
Ans. In X.509 scheme, public key certificate is associated with each user. These user certificates are assumed to be created by some trusted Certification Authority (CA) and placed in the directory by the CA or by the user. The format of X.509 certificate is shown in figure:


(iv) Virus and Intruders
Ans. Virus: A virus is a piece of code that connects to another programme. Once attached, it multiplies itself by using the program’s resources to generate copies of itself and infects other applications.
Phases of Virus: These are:
- (a) Dormant Phase: The virus is idle.
- (b) Propagation Phase: The virus places an identical copy of itself into other programmes.
- (c) Triggering Phase: The virus is activated to perform the function for which it was intended.
- (d) Execution Phase: The function is performed.
Intruders: The process of detecting and responding to malicious behaviour directed at computing and network resources is known as intrusion detection (ID). The intruder can be detected, as can the system’s consequences. Intruders can be avoided with proper intrusion detection.
(a) The three categories of ID are:
Attac detection
Intrusion detection
Misuse detection
(b) Three classes of intruders (hackers or crackers) are:
Masquerader (outsider)
Misfeasor (insider)
Clandestine user (out-orinsider).
