With our AKTU question paper and solution, you can explore the fascinating world of Web Technology. Get into beginner-friendly notes that bring the internet’s treasures to life for young explorers.
Dudes 🤔.. You want more useful details regarding this subject. Please keep in mind this as well. Important Questions For Web Technology: *Quantum *B.tech-Syllabus *Circulars *B.tech AKTU RESULT * Btech 3rd Year
Section A: Web Technology Short Answers
a. What is Domain Name System (DNS) ?
Ans. The hierarchical and decentralised naming system known as the Domain Name System is used to identify computers, services, and other resources that may be accessed via the Internet or other Internet Protocol networks. Domain names are linked to various types of information by resource records in the DNS.
b. Discuss various web project development phases.
Ans. Following are the various stages and strategies required in order to develop a web project:
Phase-I: Strategy:
- 1. Goals and objectives
- 2. Team building
- 3. Research and review
- 4. Project proposal
Phase-II: Design and specification:
- 1. Developing concepts
- 2. Content planning
- 3. Rough design
- 4. Final design
- 5. Build prototype
- 6. Prototype testing
Phase-IlI: Production or development:
- 1. Coding
Phase-IV: Testing and maintenance:
- 1. Automation testing
- 2. Manual testing
Phase-V: Register with ISP:
- 1. Buy domain name
- 2. Hoisting
Phase-VI: Launch
c. What are the difference between IP packet and Datagrams?
Ans.
| S. No. | Packet | Datagram |
| 1. | Packets are used in connection-oriented protocol communication. | Datagrams are utilized while using the connection-less protocol for communication. |
| 2. | It guarantee delivery. | It doesn’t guarantee delivery. |
d. Write HTML code for inserting image on a web page.
Ans.






e. Name two major protocols for accessing email from servers.
Ans. Two common protocols used to access email over the Internet: Simple Mail Transfer Protocol (SMTP) and Internet Message Access Protocol (IMAP).
f. Define Document Object Model (DOM).
Ans. A common object model for describing HTML or XML and similar formats, the Document Object Model (DOM), is agnostic of language and platform.
g. What is the concept behind client-server computing?
Ans. Client-server refers to a relationship between working programmes in an application, where clients request services and servers fulfill such requests.
h. Expand the term AWT. For what purpose it is being used?
Ans. The AWT stands for Abstract Window Toolkit. AWT is a library of class which provides GUI tools to develop GUI application and applet.
i. What do you understand by session tracking.
Ans. A approach to keep track of a user’s status (info) is through session tracking. In servlets, it is sometimes referred to as session management.
j. What is implicit object in JSP?
Ans. The Java objects that the JSP Container provides to the developers in each page and allows the developers to call directly without being explicitly defined are known as implicit objects. The term “pre-defined variables” also applies to JSP Implicit Objects.
Section B: Important Notes on Web Technology
a. Design HTML form for student registration with submit and reset button on it.
Ans.
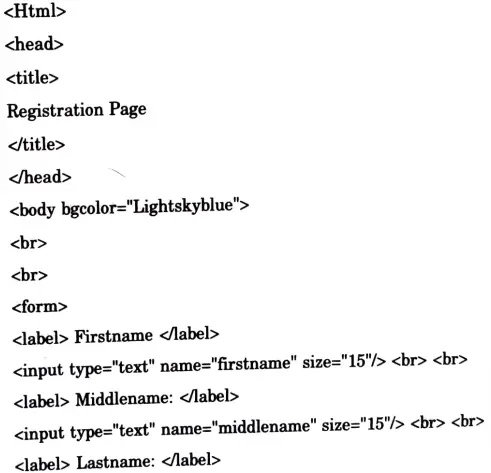








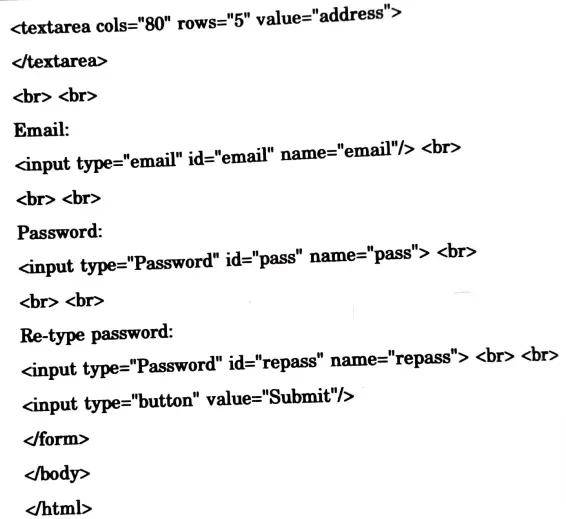


b. Explain CSS and its types with example.
Ans. CSS:
- 1. Cascading Style Sheet or CSS enables us to separate the content of HTML documents from the presentation.
- 2. A single file or a small group of files could define the presentation format for the entire website. Thus, any format or presentation changes across the website would be controlled through these CSS files.
- 3. To define styles, we use the <style> element.
- 4. To define properties for the documents, we specify the attributes for the document tags within the <style>.
- 5. When defining the style for a template HTML file, the style element is placed within the document <head> and not in the <body>.
1. Inline CSS:
a. An inline CSS is used to apply a unique style to a single HTML a element.
b. An inline CSS uses the style attribute of an HTML element.
For example: Following example sets the text color of the element to blue :
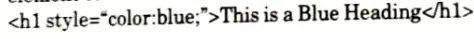
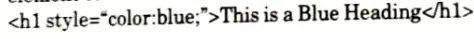
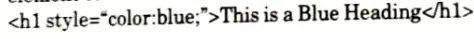
2. Internal CSS:
a. An internal CSS is used to define a style for a single HTML page.
b. An internal CSS is defined in the <head> section of an HTML page, within a <style>element.
For example:






3. External CSS:
a. An external style sheet is used to define the style for many HTML a. pages.
b. An external style sheet is used to change the look of an entire website.
c. To use an external style sheet we add a link in the section of the HTML page.
For example:



c. Explain JavaScript function and write a program to make a calculator using JavaScript.
Ans. JavaScript:
1. Functions can be defined both in the <head> and in the <body> section of a document.
2. However, to assure that the function is before it readloaded by the browser is called, it is needed to be defined in the <head> section.
3. Syntax:



4. A function with no parameters must include the parentheses () after the function name :
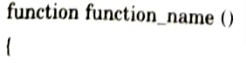
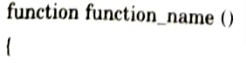
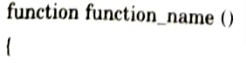



Program:









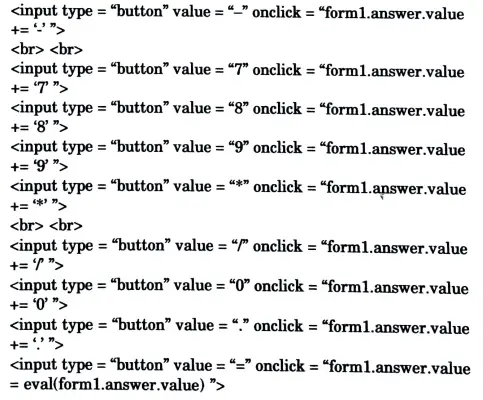





d. What are XML Parsers ? Explain the types of Parses with their advantages and disadvantages.
Ans. XML parser:
- 1. An XML parser is a software library or collection that offers client applications interfaces for interacting with XML documents.
- 2. The XML Parser is made to read XML and make it accessible to programmes.
- 3. The XML parser validates the document and examines its formatting.
There are two types of XML Parsers:
1. DOM:
- a. A common object model for describing HTML or XML and similar formats, the Document Object Model (DOM), is agnostic of language and platform.
- b. A standard for accessing documents like XML and HTML is defined by the DOM.
Advantages:
- i. The API is fairly easy to use and it supports both read and write operations.
- ii. When random access to widely separated areas of a document is needed, it is preferred.
Disadvantages:
- i. It is memory inefficient.
- ii. It is comparatively slower than other parsers.
2. SAX:
- a. SAX stands for Simple API for XML and works directly with an XML.
- b. SAX is an event-driven API that allows us to interpret a web file that uses XML.
- c. SAX takes the control of event specifies by the programmer and handles the situation.
Advantages:
- i. It is simple and memory efficient.
- ii. It is very fast and works for huge documents.
Disadvantages:
- i. It is event based so its API is less intuitive.
- ii. Clients never know the full information because the data is broken into pieces.
e. What are the advantages and drawback of an applet? Write a Java program to create an applet and perform event handling on it.
Ans. Advantages of applets:
- 1. Applets are platform independent.
- 2. Applets are quite secure and safe to use.
- 3. Applets cache quickly.
- 4. Applet increase interactivity for users.
- 5. Database integration is another important advantage of applets.
Drawbacks of applets:
- 1. Applets do not access client-side resources, like such as file, operating system.
- 2. Applet cannot work with native methods.
- 3. Applet can only extract information about client-machine ie., its name, Java version, OS, version etc.
- 4. Mobile browsers which are running on IOS or Android do not support applets.
Program:















Section 3: Enterprise Java Bean
a. Create an HTML page name as “table html” to display your class time table.
Ans.
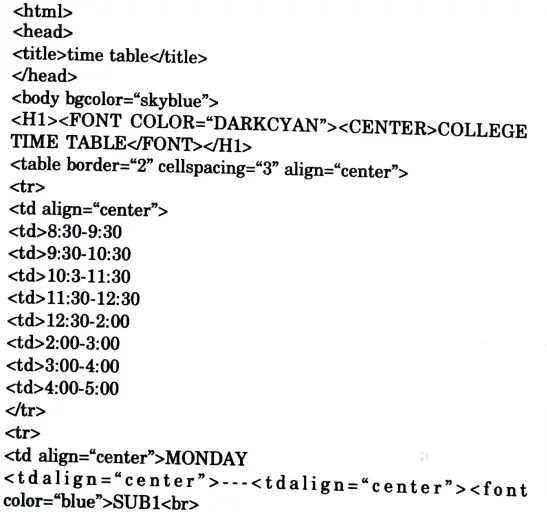


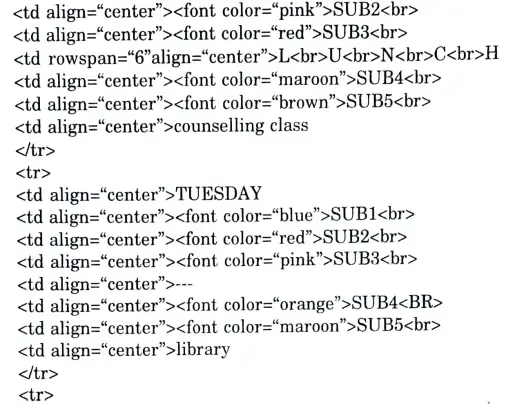








b. Explain Enterprise Java Bean in detail and explain its types. Create a message driven java bean.
Ans. Java Beans:
- 1. Java Beans are classes which encapsulate several objects into a single object.
- 2. It helps in accessing the objects from multiple places.
- 3. It is a portable, platform independent model written in Java.
Steps used to create Java Bean:
Step 1: Put source code into a file named “SimpleBean.java”:



Step 2: Compile the file:
javac SimpleBean.java
Step 3: Create a manifest file, named “manifest.tmp”:
Name: SimpleBean.class
Java-Bean: True
Step 4: Create the JAR file, named “SimpleBean jar”:
jar cfm SimpleBean.jar manifest.tmp SimpleBean.class
Then, verify that the content is correct by the command “jar tf
SimpleBean.jar”.
Step 5:
1. Start and run the Bean Box.
2. Load JAR file into Bean Box by selecting “Loadjar….” under the File menu.
Step 6:
1. After the file selection dialog box is closed. Then “SimpleBean” appear at the bottom of the toolbox window.
2. Select SimpleBean.jar.
3. Cursor will change to a plus. In the middle BeanBox window, we can now click to drop in what will appear to be a coloured rectangle.
Step 7: Try changing the red box colour with the Properties windows.
Step 8: Choose “Events” under the “Edit” menu in the middle window to see what events SimpleBean can send. These events are inherited from java.awt.Canvas.
Role of introspection in Java Bean:
1. Java Beans, which constitute the component model of Java, are the context in which introspection is used.
2. A Java Bean can access the properties, methods, and events of other beans at runtime thanks to the introspection capability.
3. Because of this, developers can design and create their own beans without being aware of the specifics of others.
Steps to build application using BDK:
Step 1: Create a directory for the new bean.
Step 2: Create the Java source file(s).
Step 3: Compile the source file(s).
Step 4: Create a manifest file.
Step 5: Generate a JAR file.
Step 6: Start the BDK.
Step 7: Test the newly created Java Bean.
Section 4: String Handling and Event Handling
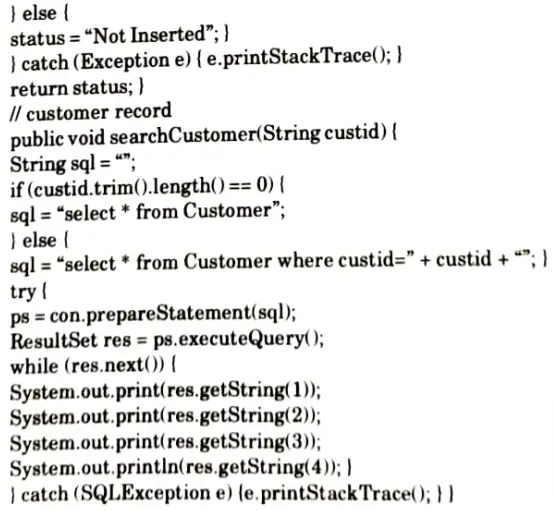
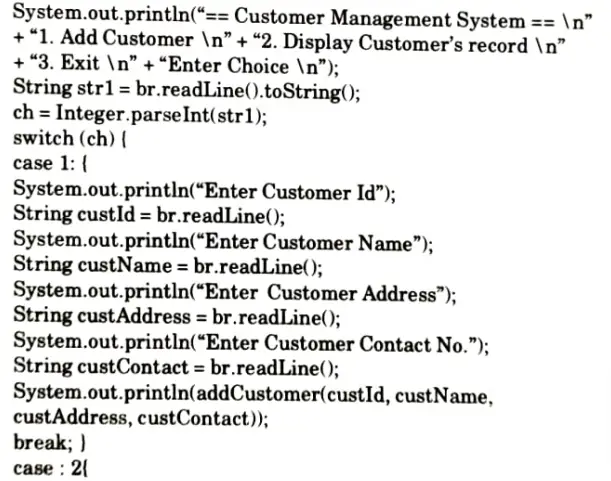
a. What is JBDC? Explain the driver used in JBDC. Write JBDC program to insert and display the record of employees using prepared statement.
Ans. JDBC:
- 1. JDBC (Java Database Connectivity) is a Java API for managing database connections, sending commands and queries, and handling result sets that come from the database.
- 2. Both JDBC driver makers and application developers can benefit from this technology.
- 3. JDBC is specifically used to connect to the RiDBMS packages by using the appropriate JDBC driver.
Drivers in JDBC:
1. JDBC-ODBC bridge driver (Type 1 driver):
a. These drivers are the bridge drivers such as JDBC-ODBC bridge.
b. These drivers rely on an intermediary such as ODBC to transfer the SQL calls to the database.
c. Bridge drivers often rely on native code, although the JDBC-ODBC library native code is part of the Java-2 virtual machine.
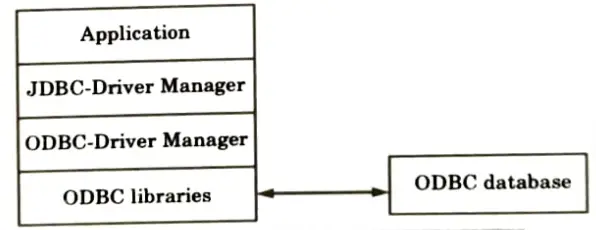


2. Native API partly Java driver (Type 2 driver):
a. A native API is partly a Java driver. It uses native C language library calls to translate JDBC to native client library.
b. These drivers are available for Oracle, Sybase, DB2 and other client library based RDBMS.
c. Type 2 drivers use native code and require additional permission to work in an Applet.
d. A Type 2 driver might need client-side database code to connect over the network.
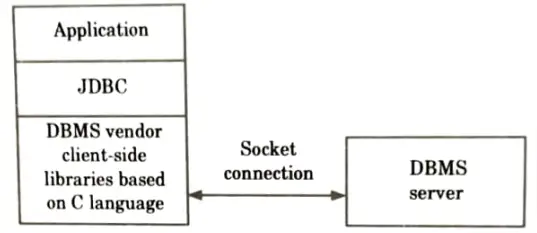


3. JDBC net pure Java driver (Type 3 driver):
a. JDBC net pure Java driver consists of JDBC and DBMS independent protocol driver.
b. Here the calls are translated and sent to middle tier server through the socket.
c. The middle tier contacts the database.
d. Type 3 drivers call the database API on the server.
4. Native protocol pure Java driver (Type 4 driver):
a. A native protocol Java driver contains JDBC calls that are converted directly to the network protocol used by the DBMS server.
b. This driver interacts directly with database.
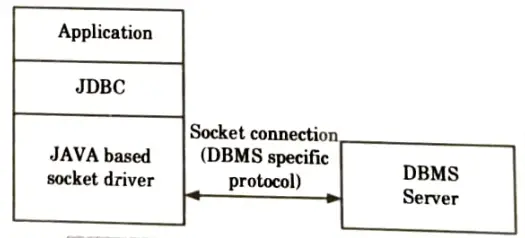


c. It does not require any native database library. So, it is also called thin driver.
Program:
















b. Explain string handling and event handling in Java.
Ans. String handling:
- 1. String handling is a process of performing different operation such as concatenation, comparison on the string.
- 2. Following are the method used in string handling:
- a. Java string length(): The Java string length() method returns the length of the string. It returns count of total number of characters present in the string.
- b. Java string compareTo(): The Java string compareTo() method compares the given string with current string. It returns positive number, negative number or zero.
- c. Java string concat(): The Java string concat() method combines a specific string at the end of another string and returns a combined string.
- d. Java string replace(): The Java string replace() method returns a string, replacing all the old characters to new characters.
- e. Java string equals(): The Java string equals() method compares the two given strings on the basis of content of the string. If all the characters are matched, it returns true else it will return false.
- f. Java string contains(): The Java string contains() method searches the sequence of characters in the string. If the sequences of characters are found, then it returns true otherwise returns false.
Event handling:
- 1. An event happens when something changes within a graphical user interface.
- 2. We can say that events are objects in Java. It comes under some classes stored in java. util. EvenObject.
- 3. The Abstract Window Toolkit (AWT) uses event driven programming to do processing of user actions, one that underlies all modern window systems programming.
- 4. An event describes as a particular user action.
- 5. The Java run time notifies the program when an interesting event occurs.
- 6. For example, events occur when a user clicks on a button, clicks on a combobox, or types characters into a text field, such as in the following:
- a. For a button, the event that is fired is the Actionlistener.
- b. For a text field, it is the KeyEvent.
Section 5: Session and Cookies
a. What is the difference between Session and Cookies? Write a servlet program for servlet login and logout using cookies.
Ans.
| S. No. | Session | Cookies |
| 1. | Sessions are stored in server. | Cookies are stored in the user’s browser. |
| 2. | A session is available as long as the browser is opened. User can not disable the session. | Cookies can keep information in the user’s browser until deleted by user or set as per the timer. |
| 3. | It will be destroyed if we close the browser. | It will not be destroyed even if we close the browser. |
| 4. | It can store any object. | Cookies can only store string. |
| 5. | Session cannot be same for future reference. | We can save cookies for future reference. |
Program:



link.html:



login.html:



LoginServletjava:
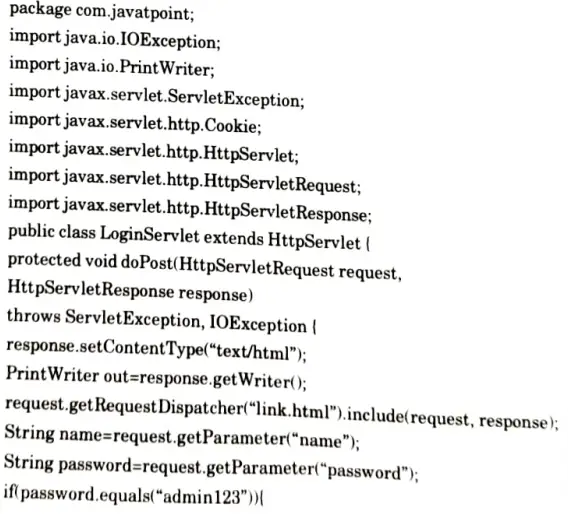





LogoutServlet.java:
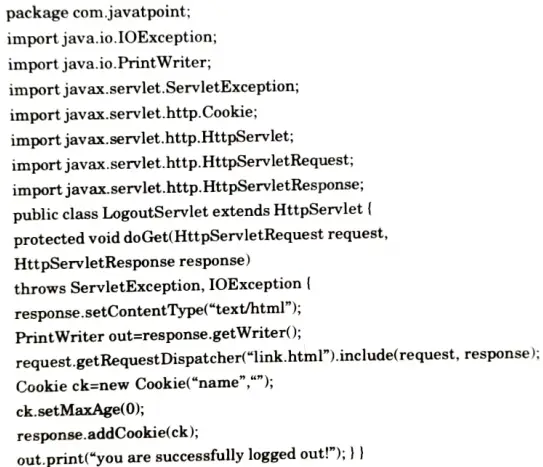


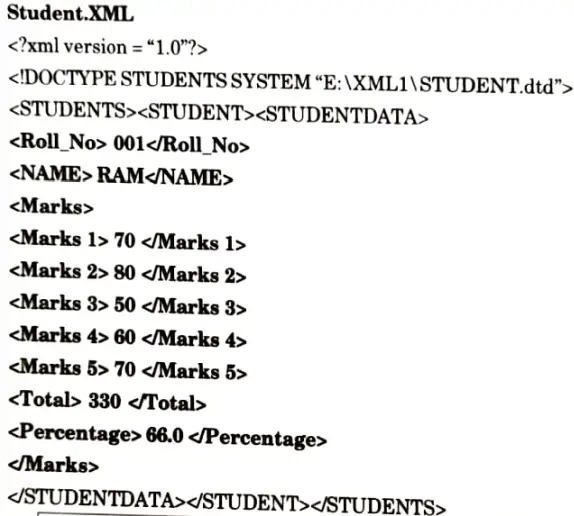
b. What is XML ? Create a XML document of 10 students of third year CSE. Add their roll number, marks obtained in 5 subjects, total marks and percentage.
Ans. XML:
- 1. The role of a DTD is to define the legal building blocks of an XML document.
- 2. It defines the document structure with a list of legal elements.
- 3. A DTD can be declared inline in our XML document, or as an external reference.
XML document:


Section 6: JSP Architecture
a. Discuss Servlet and its life cycle in detail. How do you create a servlet?
Ans. Life cycle of Servlet:
Stages of the Servlet life cycle:
1. Loading a Servlet:
- a. The first stage of the Servlet life cycle involves loading and initializing the Servlet by the Servlet container.
- b. The Servlet container performs two operations in this stage :
- i. Loading: Loads the Servlet class.
- ii. Instantiation: Creates an instance of the Servlet. To create a new instance of the Servlet, the container uses the no argument constructor.
2. Initializing a Servlet:
- a. After the Servlet is instantiated successfully, the Servlet container initializes the instantiated Servlet object.
- b. The container initializes the Servlet object by invoking the Servlet.init(ServletConfig) method which accepts ServletConfig object reference as parameter.
3. Handling request:
- a. After initialization, the Servlet instance is ready to serve the client requests.
- b. The Servlet container performs the following operations when the Servlet instance is located to service a request:
- i. It creates the ServletRequest and ServletResponse objects.
- ii. After creating the request and response objects it invokes the Servlet.service(ServletRequest, ServletResponse) method by passing the request and response objects.
4. Destroying a Servlet:
- a. When a Servlet container decides to destroy the Servlet, it performs the following operations,
- i. It allows all the threads currently running in the service method of the Servlet instance to complete their jobs and get released.
- ii. After currently running threads have completed their jobs, the Servlet container calls the destroy() method on the Servlet instance.
- b. After the destroy() method is executed, the Servlet container releases all the references of this Servlet instance so that it becomes eligible for garbage collection.
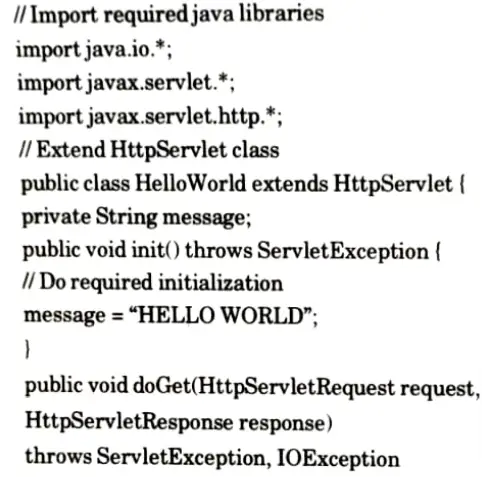
Servlet for displaying “HELLO WORLD”:





b. Explain JSP Architecture and explain the JSP Processing in detail.
Ans. JSP architecture:
- 1. Java Server Pages are part of a 3-tier architecture.
- 2. A server (application or web server) supports the Java Server Pages.
- 3 This server will act as a mediator between the client browser and a database.
- 4. The following diagram shows the JSP architecture:
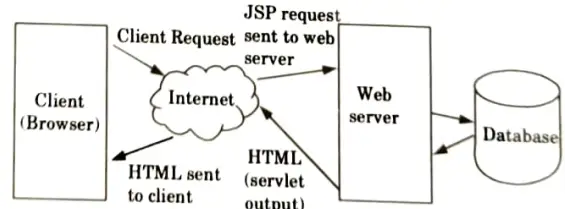


- a. The user accesses a JSP page and submits the request through a web browser on the internet.
- b. The web server receives the JSP request.
- c. The web server accepts the JSP file that was requested and sends it to the JSP Servlet Engine.
- d. The JSP file is parsed if it has been called for the first time; otherwise, a servlet is created. The JSP file must then be converted into a servlet as the next step. The resulting servlet output is transmitted from the web server to the user’s web browser across the Internet.
- e. The user’s web browser is now used to show the HTML results in the last phase.
JSP processing:
- 1. The original request is forwarded to the servlet engine during JSP processing, where the servlets are compiled up to an executable class and then executed on the web server.
- 2. JSP pages can be processed using JSP container only.
- 3. Following are the steps that need to be followed while processing the request for JSP page:
- a. Client makes a request for required JSP page to the server.
- b. The server must have JSP container so that JSP request can be processed.
- c. On receiving request the JSP container searches and then reads the desired JSP page.
- d. Then JSP page is converted to corresponding servlet. Basically any JSP page is a combination of template text and JSP element.
- e. Every template text is translated into corresponding print in statement.
Section 7: Internet Addressing
a. Explain Internet Addressing. How will you identify IP Class?
Ans. Internet addressing:
- 1. Each computer on a network is uniquely identified by its IP address, which is a network layer address.
- 2. Logical IP addresses are used to identify each TCP/IP host.
- 3. An IP address locates a system on the network and reveals its location. An IP address needs to be globally distinct and have a standard structure.
- 4. Each IP address includes a network ID and a host ID.
- i. Systems that are situated on the same physical network ID are identified by the network ID, commonly referred to as a network address. A network ID that is specific to the internetwork is required.
- ii. A workstation, server, router, or other TCP/IP host within a network is identified by its host ID, which is also referred to as its host address. Each host’s address must be distinct from the network ID.
- 5. The use of the term network ID refers to any IP network ID, whether it is class-based, a subnet, or a supernet.



- 6. An IP address is 32 bits long. It is a common practice to segment the 32 bits of the IP address into four 8-bit fields called octets.
- 7. Each octet is converted to a decimal number (the base 10 numbering system) in the range 0-256 and separated by a period (a dot). This formal is called dotted decimal notation.
Classification: IP address is classified as:
1. Class A:
- i. Class A addresses are assigned to networks with a very large number of hosts.
- ii. The high-order bit in a class A address is always set to zero.
- iii. The next seven bits (completing the first octet) complete network ID. The remaining 24 bits (the last three octets) represent the host ID.
- iv. This allows for 126 networks and 16,777,214 i.e., 224 hosts per network.
2. Class B:
- i. Class B addresses are assigned to medium-sized to large-sized networks.
- ii. The two high-order bit in a class B address are always set to binary 10.
- iii. The next 14 bits (completing the first two octets) complete the network ID. The remaining 16 bits (last two octets) represent the host ID.
- iv. This allows for 16,384 networks and 65,534 hosts per network.
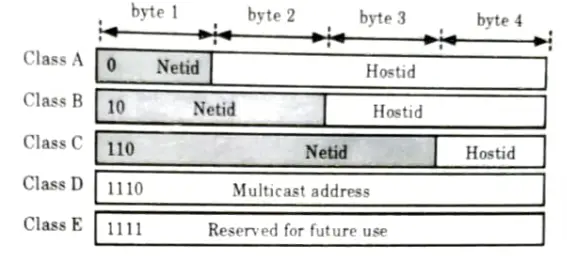


3. Class C:
- i. Class C addresses are used for small networks.
- ii. The three high-order bits in a class C address are always set to binary 110.
- iii. The next 21 bits (completing the first three octets) complete the network ID. The remaining 8 bits (last octet) represent the host D.
- iv. This allows for 2,097, 152 networks and 254 hosts per network.
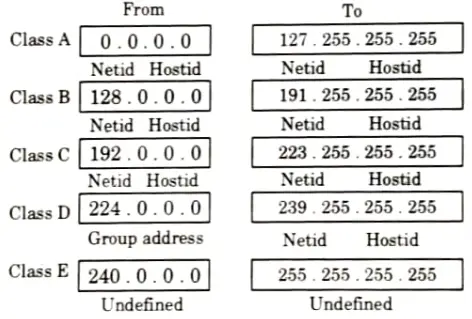


4. Class D:
- i. Class D addresses are reserved for IP multicast addresses.
- ii. The four high-order bits in a class D address are always set to binary 1110.
- iii. The remaining bits are for the address that interested hosts wii recognize.
- iv. Microsoft supports class D addresses for applications to multicast data to multicast-capable hosts on an internet work.
5. Class E: Class E addresses are experimental addresses reserved for future use. The high-order bits in a class E address are set to 1111.
b. How exceptions are handled in java ? Explain in detail with examples.
Ans. An exception is an unintended or unexpected occurrence that takes place at runtime, or when a programme is being executed, and which interferes with the regular flow of its instructions.
Exception handling:
- 1. Exception handling provides a type-safe, integrated approach for handling unusual problems that arise while executing a program.
- 2. To handle the exceptions, exception handling mechanism is designed.
- 3. The mechanism suggests a separate error handling code that performs the following tasks:
- a. Find the problem (Hit the exception)
- b. Inform that an error has occurred (Throw the exception)
- c. Receive the error information (Catch the exception)
- d. Take corrective actions (Handle the exception)
Java exception handling is managed by the following keywords:
1. Try:
- a. Java uses keyword “try” to preface a block of code that is likely to cause an error condition and “throw” an exception.
- b. The try block can have one or more statements that could generate an exception.



- c. If any one statement in the block raises an exception, the remaining statements are skipped, and the try block is followed by the catch block.
- d. A compilation error will occur if a try statement is not followed by at least one catch statement.
2. Catch:
- a. An exception thrown by the try block is caught and handled properly by a catch block, which is defined by the keyword “catch.” In addition, the try block is followed immediately by the catch block.
- b. One or more statements in the catch block may be required to handle the exception.
- c. A single parameter, a reference to the kind of exception object thrown by the try block, is supplied to the catch statement.
- d. The exception is caught and the lines in the catch block are executed if the catch argument fits the type of the exception object.
3. Finally:
- a. When none of the a. prior catch statements are able to handle an exception, Java allows additional statement known as a finally statement.
- b. Finally block can be used to handle any exception generated within a try block.
- c. It may be added immediately after the try block or after the last catch block as follows:
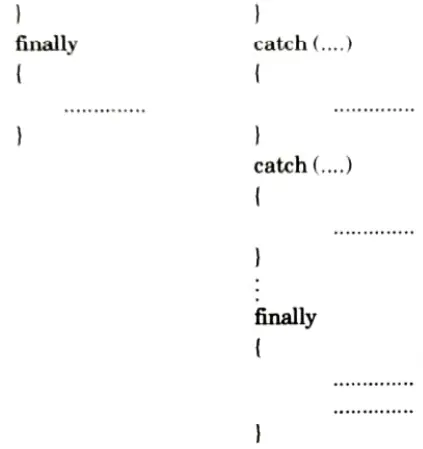


4. Throw:
a. Java supports “throw keyword” which is used if we want to throw our own exceptions.
b. We can do this by using the keyword throw as follows:
throw new Throwable_subclass;
No, it is not essential to catch all type of exceptions.
For example:



Output:




6 thoughts on “Web Technology AKTU SOLVED QUESTION PAPER”